
Best practices in industrial cybersecurity: tips and importance!
In a world where Industry 4.0 is revolutionizing production chains, industrial cybersecurity has become essential. The integration of connected technologies exposes industrial systems, historically isolated, to increasingly sophisticated cyber threats. These attacks can disrupt operations, cause significant financial losses, and jeopardize the sustainability of businesses. This article guides you through best practices and highlights the critical importance of industrial cybersecurity. You will discover why securing your infrastructure is crucial in the face of major risks related to cyber threats. We will provide concrete recommendations to protect your facilities and reduce vulnerabilities in your critical systems. Finally, key solutions will be discussed to secure your sensitive data and ensure operational resilience.
The Importance of Industrial Cybersecurity
The Rise of Cyber Threats in Industry
With the advent of Industry 4.0, IIoT technologies are revolutionizing production chains and enhancing operational efficiency. However, they also expose industrial companies to new forms of cyber threats targeting their critical systems. Ransomware, for example, can encrypt sensitive data and demand a ransom for its restoration. Distributed Denial of Service (DDoS) attacks aim to overload connected systems, causing essential industrial processes to halt. Malware can compromise SCADA systems, manipulating production parameters to create defects in finished products.
The importance of industrial cybersecurity lies in the ability to protect these infrastructures from such complex cyberattacks. Without adequate security measures, companies risk facing disastrous financial, operational, and strategic consequences. Fortunately, there are best practices to mitigate these risks.
A Direct Impact on Operational Continuity
A cyberattack can cripple a production chain, leading to factory shutdowns and significant financial losses. In 2022, Toyota halted production at all its Japanese factories due to a network attack. This cyberattack targeted one of its suppliers, causing major disruptions across the entire production chain. The incident highlighted the vulnerability of industrial networks to threats originating from unsecured external partners.
Such an event demonstrates the importance of industrial cybersecurity in protecting critical operations of manufacturing companies. Without effective protection, a single attack can jeopardize an organization’s production and reputation.
Protecting Critical Data and Processes
Industrial systems go far beyond simply securing equipment and machinery. These infrastructures handle highly sensitive data, such as manufacturing processes, production schedules, and customer information. Protecting this data is essential to prevent theft or compromise of sensitive information.
One of the best practices in industrial cybersecurity is the ability to safeguard these critical resources, which are essential for competitiveness and operational continuity. Beyond data, critical processes themselves are prime targets. For example:
- An attack can manipulate production parameters to cause defects in finished products.
- It can also disrupt production lines by compromising SCADA (Supervisory Control And Data Acquisition) or PLC (Programmable Logic Controller) systems.
These disruptions can lead to massive financial losses and a loss of customer trust. Implementing appropriate measures once again highlights the importance of industrial cybersecurity. It is essential to maintain business competitiveness and sustainability.
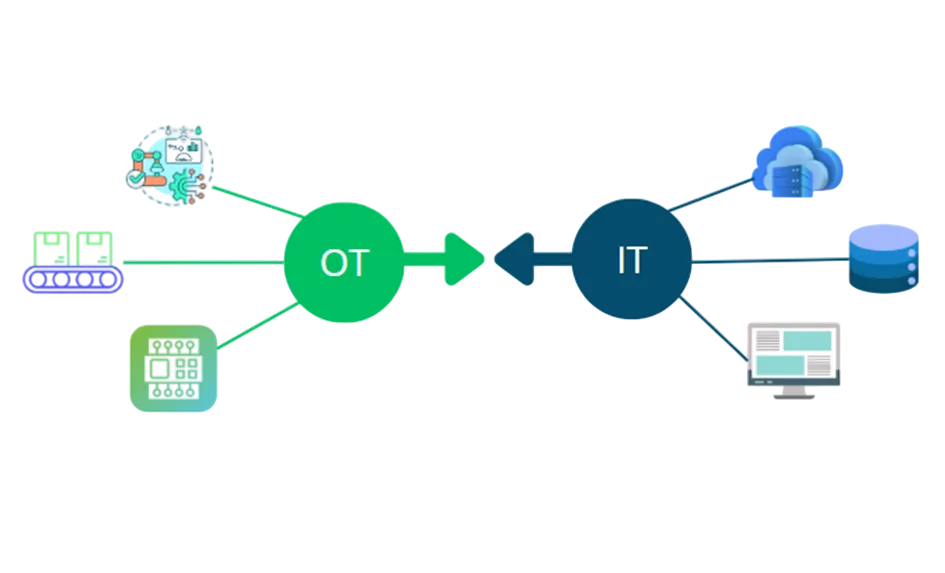
IT/OT Convergence: A New Challenge
IT/OT convergence is transforming the landscape of industrial cybersecurity by integrating information and operational technologies. Historically isolated, OT (Operational Technology) systems are now connected to IT (Information Technology) networks, exposing new entry points for cyberattacks. This interconnection enhances the efficiency of industrial processes but requires security measures tailored to both environments. Threats targeting OT equipment, such as programmable logic controllers, can lead to critical shutdowns or major disruptions.
To secure this convergence, it is essential to implement a security policy that considers the specificities of each infrastructure.
5 Best Practices for Industrial Cybersecurity
Best Practice #1: Establish and Maintain an Inventory of Network-Connected Devices
The first step to strengthening industrial cybersecurity is to establish a complete inventory of all devices connected to the network. This includes HMIs, programmable controllers, IIoT equipment, and more. This inventory provides a clear visualization of the entire IT and operational infrastructure. Knowing exactly which devices are present helps identify critical assets and better plan protection measures. It forms a solid foundation for proactive industrial security management and facilitates well-informed decision-making when needed.
Best Practice #2: Control Workstation Modification Permissions
Restricting modification permissions on workstations is essential to prevent unauthorized access. Implementing rigorous identity management, such as IAM (Identity Access Management), is crucial for controlling access. This system allows precise definition of who can access specific resources. The use of strong passwords and multi-factor authentication (MFA) further enhances security. For example, MFA can involve a code sent via SMS or an authentication app. These solutions make hacking attempts more difficult and help protect industrial systems from cyber threats.
Best Practice #3: Train Employees on Cybersecurity Practices
Operators are the first line of defense against cyberattacks. It is essential to train them in good cybersecurity practices. For example, they should create strong passwords and recognize phishing attempts. They must also learn to avoid fraudulent websites and not mix personal and professional usage. Caution with public Wi-Fi networks and unverified USB drives should also be emphasized. Ongoing training helps reduce human errors, which are often the root cause of security breaches.
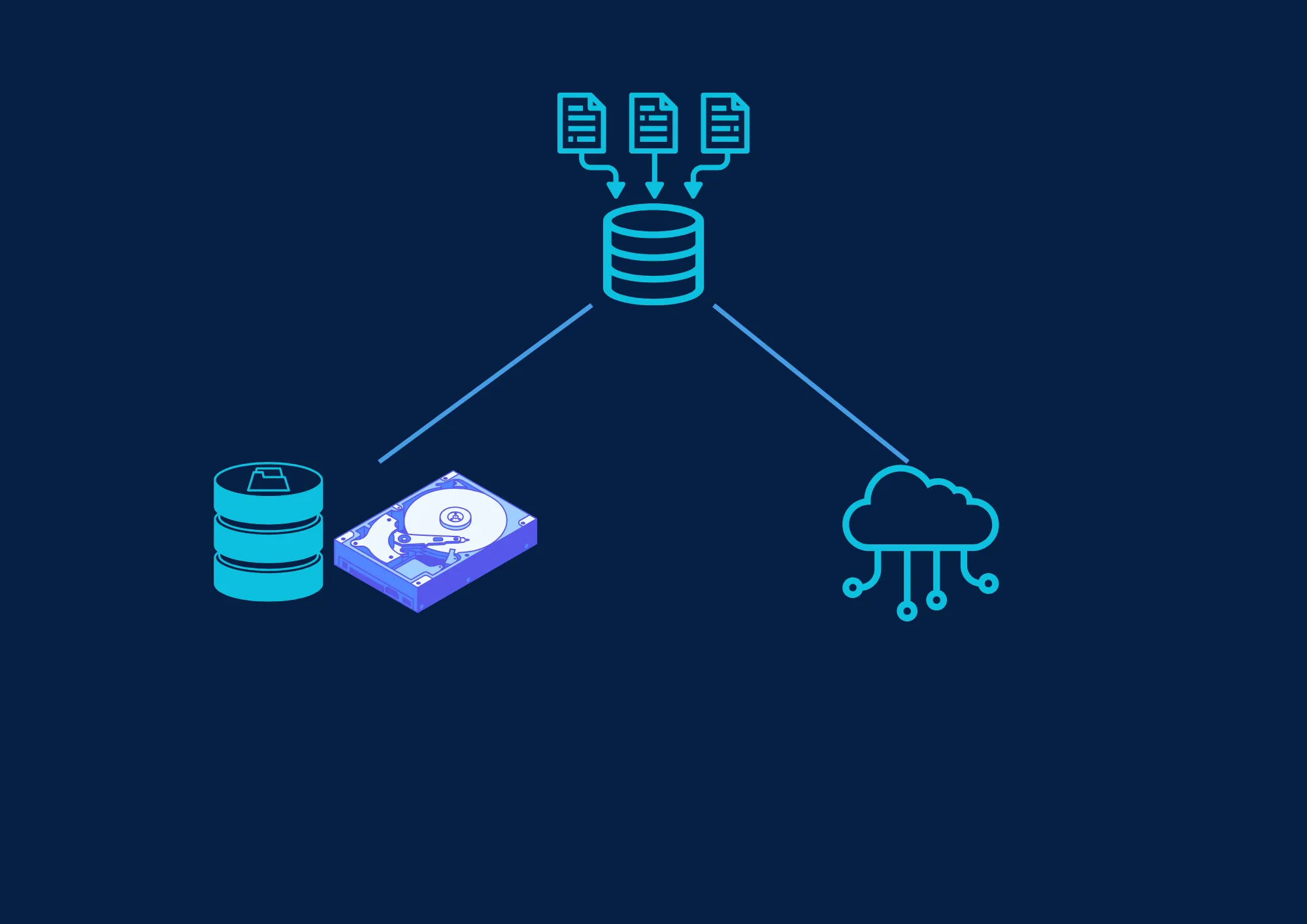
Best Practice #4: Perform Regular Data Backups in Secure Environments
Performing regular backups is crucial to preserving data integrity in case of an incident. These backups should be stored in secure environments, on both physical media and the cloud. An effective strategy follows the "3-2-1" rule, which is essential for optimal protection. This rule involves keeping three copies of data, on two different storage media, with one stored offsite or in the cloud. This approach ensures quick and complete data recovery in the event of an industrial cyberattack or system failure.
Best Practice #5: Implement a Security Incident Management Policy
An incident management policy is essential to respond quickly to an industrial cyberattack. This includes rapid anomaly detection and identifying signs of intrusion. An appropriate response must be in place to minimize impact and contain damage. After an incident, preventive measures such as the Disaster Recovery Plan (DRP) and the Business Continuity Plan (BCP) are crucial to prevent recurrence. This structured process strengthens the company’s resilience and minimizes the impact of cyberattacks on operations.
Our Solutions for Your Industrial Cybersecurity
Protecting your industrial systems requires a comprehensive approach tailored to the specific challenges of OT environments. Dative offers complete and customized solutions to ensure the security of your industrial infrastructures.
Mapping and Inventory
Protecting your industrial systems requires a comprehensive approach tailored to the specific challenges of OT environments. Dative offers complete and customized solutions to ensure the security of your industrial infrastructures.
Cybersecurity Assessment
We conduct an in-depth assessment of your cybersecurity posture. This includes identifying vulnerabilities, verifying compliance with standards and regulations (such as the NIST Framework and IEC 62443), and analyzing risks specific to your processes. Our assessment provides you with a clear report and tailored recommendations to enhance your security.
Industrial Network Security
OT networks require specific security measures to prevent intrusions or the spread of threats. We implement network segmentation solutions to isolate critical systems, thereby limiting attack risks. We enforce strict access controls to restrict access to sensitive systems to authorized personnel only. These combined solutions provide strong protection for industrial networks, reducing cyberattack entry points.
Deployment of IDS Probes
IDS (Intrusion Detection System) probes help detect abnormal behaviors on your industrial networks. These tools are essential for real-time detection of malicious activities, providing proactive protection against cyber threats.
Vulnerability Monitoring
Threats constantly evolve, and staying informed is crucial. Our vulnerability monitoring service continuously tracks newly discovered flaws in your systems. We keep you updated on available patches and assist you in their implementation.
Security Equipment and Console Management
Ensuring effective cybersecurity requires centralized management of security equipment (firewalls, IDS probes, etc.). We handle the configuration, monitoring, and continuous optimization of these systems to keep them effective against emerging threats.
For more information about our services, contact our experts.
Conclusion
Our industrial cybersecurity experts help you strengthen your resilience against cyber threats. Our solutions ensure the security and operational continuity of your industrial systems.
Industrial cybersecurity is no longer optional. It is essential to protect your control systems. It guarantees operational continuity and safeguards critical company data.
By adopting best practices in industrial cybersecurity, you can protect yourself from cyber threats. Implementing the right solutions strengthens your security and ensures the sustainability of your industrial infrastructures.
Take the necessary steps today to secure your industrial systems with DATIVE.





