
How can you anticipate cyber attacks on your industrial infrastructure?
Industrial infrastructures have become prime targets for cyber attacks. Often orchestrated by malicious actors, including state-sponsored groups. The impact of these attacks can be devastating, both operationally and financially.Anticipating cyber attacks on industrial infrastructures means putting in place solid defences. This article guides you through the risks, solutions and best practices for securing your systems.
What is a cyber attack on an industrial infrastructure?
Definition: An industrial cyber attack is a malicious attempt to compromise industrial control systems (ICS). It aims to gain illegal access to networks or devices in order to steal, modify or destroy sensitive data.
The growing interconnection of OT and IT networks is increasing the exposure of critical industrial infrastructures to cyber threats. Ces systèmes, essentiels à la production d’énergie, au transport et à la fabrication, deviennent des cibles majeures.
Nearly 60% of cyber attacks on critical infrastructure are carried out by state-affiliated groups. These groups often seek to destabilise vital sectors in order to achieve geopolitical objectives. The average cost of a data breach reached 4.45 million dollars in 2023.

Examples of industrial cyberattacks
Cyber attacks on industrial infrastructures can take a variety of forms. Among the most common are the following examples of industrial cyber attacks:
- Ransomware: These attacks encrypt data, making operations impossible until a ransom is paid. Attackers target corporate networks to demand money in exchange for the decryption key.In 2021, the ransomware attack on Colonial Pipeline paralyzed the largest fuel network. This attack led to rising gas prices and a regional shortage. It cost over $4.4 million in ransom.
- Industrial Control System (ICS) Intrusions: These attacks target control systems to manipulate industrial processes in real time. This can cause major accidents or prolonged outages.Stuxnet, a virus discovered in 2010, targeted centrifuges in Iran’s nuclear program. It altered their speed without operators noticing, irreparably damaging them.
- Industrial Espionage: This type of attack aims to steal sensitive information, such as production data or trade secrets. These details are often used to benefit competitors.In 2014, Sony Pictures suffered a sophisticated cyberattack where sensitive data was stolen. This included film scripts, personal information about employees, and internal emails.
In this section, we will look at three major risks associated with cyber attacks on industrial infrastructures.
Financial losses
Cyber attacks cause considerable direct and indirect financial losses to critical industrial infrastructures. Production interruptions caused by ransomware result in losses of up to several million euros. These incidents include remediation costs: checking backups, replacing systems, audits and security updates.
The indirect costs include fines for non-compliance, high insurance premiums, as well as legal fees. These expenses are in addition to the costs related to loss of revenue during business interruptions.
For small and medium-sized businesses, these costs can be unbearable, jeopardizing their financial viability. These businesses often have limited resources to absorb such losses and strengthen their defenses. It is crucial to invest in robust cybersecurity solutions and proactive strategies. This helps reduce the financial risks associated with industrial cyberattacks.
Business Activity Pause
A cyberattack on critical industrial infrastructures can completely cripple a company’s operations. The attack disrupts production, inventory management, and order tracking. This leads to a loss of visibility over key processes, directly impacting the supply chain. Delivery times are extended, affecting customer satisfaction and the company’s image.
Online sales and other business opportunities are also compromised, amplifying the losses. Interruptions can last for weeks or even months, significantly increasing the loss of revenue. The loss of employee productivity and the overall slowdown of activities exacerbate these disruptions.
The impact becomes more significant as recovery costs increase. The consequences of such paralysis are not limited to direct losses. They also affect relationships with partners, customers, and shareholders. The ability to quickly restore operations becomes essential to minimize long-term damage.

Loss of Reputation
Cyberattacks have a profound impact on the reputation of industrial companies. In cases of compromise of sensitive data, customer trust is quickly eroded. The loyalty of existing customers is undermined, and acquiring new contracts becomes more challenging. A cyberattack reveals a lack of cybersecurity diligence, thereby alarming investors and partners.
This lack of trust can lead to a growing loss of interest in the company, resulting in a devaluation of the brand. The company risks losing business opportunities and its competitive position in the market. Employees also feel the effects of the crisis, particularly on their morale. The stress caused by managing the attack disrupts the smooth running of operations.
This can lead to further delays, worsening the company’s operational and financial situation. Reputation is a crucial intangible asset, and restoring it after a cyberattack can take years.
Assess the security of your industrial infrastructures with our experts. Contact us now.
7 Tips to Protect Your Industrial Infrastructures from Cyberattacks
The cybersecurity of industrial infrastructures relies on proactive risk management, according to the NIST Cybersecurity Framework, which is based on five essential functions: Identify, Protect, Detect, Respond, and Recover. These functions form a comprehensive approach to prepare, defend, and recover from cyberattacks.

1. Map/Inventory Your Assets
To protect yourself, it is essential to have an accurate knowledge of your digital assets. Do you really know your system? Do you know how many devices are connected and where they are located? Most industrial companies cannot answer these fundamental questions with precision. A detailed mapping and inventory allow for a clear definition of the scope and better security of the infrastructures.
2. Conduct a Cybersecurity Audit
A cybersecurity audit helps identify vulnerabilities and specific risks in your system. This comprehensive analysis identifies potential weaknesses and evaluates the sensitive areas of your industrial infrastructures. It includes the examination of networks, processes, technologies, and existing security policies. Conducting an audit provides a clear view of your current posture and the necessary improvements. This approach results in a precise roadmap to effectively strengthen your cybersecurity.
Request an industrial cybersecurity audit to build an action plan tailored to your needs.
3. Train Employees
Employee training is essential to protect your infrastructures against cyberattacks. Human errors are often the cause of cyberattacks, such as clicking on malicious links. Regular sessions on best practices and threat recognition significantly reduce this risk. The training should include handling sensitive data and recognizing phishing attacks.
4. Back Up and Recover Data
Rapid incident detection and quick data recovery are essential in a cybersecurity framework. Regular and secure backups of critical data allow systems to be restored after a cyberattack. These backups must be frequently verified to ensure they remain intact and accessible when needed. This is part of the recover function, which ensures the resilience of infrastructures during a crisis. A strong recovery strategy limits the impact of attacks and enables rapid restoration of operations. This reduces downtime and ensures business continuity despite potential threats.
Good backup practice - 3-2-1 strategy: keep three copies of your data, on two different media (e.g., hard drives and cloud), and one copy off-site. This approach enhances the resilience of your backups.
5. Implement a Business Continuity and Disaster Recovery Plan
A well-defined Business Continuity Plan (BCP) and Disaster Recovery Plan (DRP) are crucial. They outline the necessary actions to maintain critical operations during a cyberattack. These plans help prioritize and coordinate efforts during the crisis. They ensure a quick recovery after the incident and minimize the impact on operations. It is essential to regularly update these plans to ensure their effectiveness. Test your BCP and DRP regularly to verify their validity and effectiveness in real-life situations.
6. Conduct Attack Simulations
Attack simulations are an effective way to detect weaknesses in your security. Penetration tests and exercises help evaluate your infrastructure's responsiveness to cyber threats. These tests not only check defense mechanisms but also assess your team's preparedness for attacks. This minimizes the impact of intrusions and improves crisis management. These exercises help identify vulnerabilities that automated solutions may not detect. They thus help you strengthen your defenses accordingly, ensuring better resilience.
7. Equip Yourself with the Right Software
To protect your infrastructures against cyber threats, it is crucial to use appropriate security tools. NIST recommends using firewalls, antivirus software, and intrusion detection systems (IDS/IPS). These tools play a key role in defending industrial networks and systems. However, they must be regularly updated to address evolving threats. The integration of real-time monitoring helps quickly detect suspicious activities. This aids in responding proactively and minimizing the impact of cyberattacks.
The Industrial Cybersecurity Experts at DATIVE deploy tailored cybersecurity solutions for industrial networks.
Contact us for more information
Solutions Available to Anticipate Industrial Cyberattacks
DATIVE offers a comprehensive industrial cybersecurity solution, tailored to each specific infrastructure. Our services include risk assessment, securing industrial networks, and deploying robust industrial cybersecurity solutions. We integrate cybersecurity software certified by ANSSI, ensuring tools that comply with the highest standards.

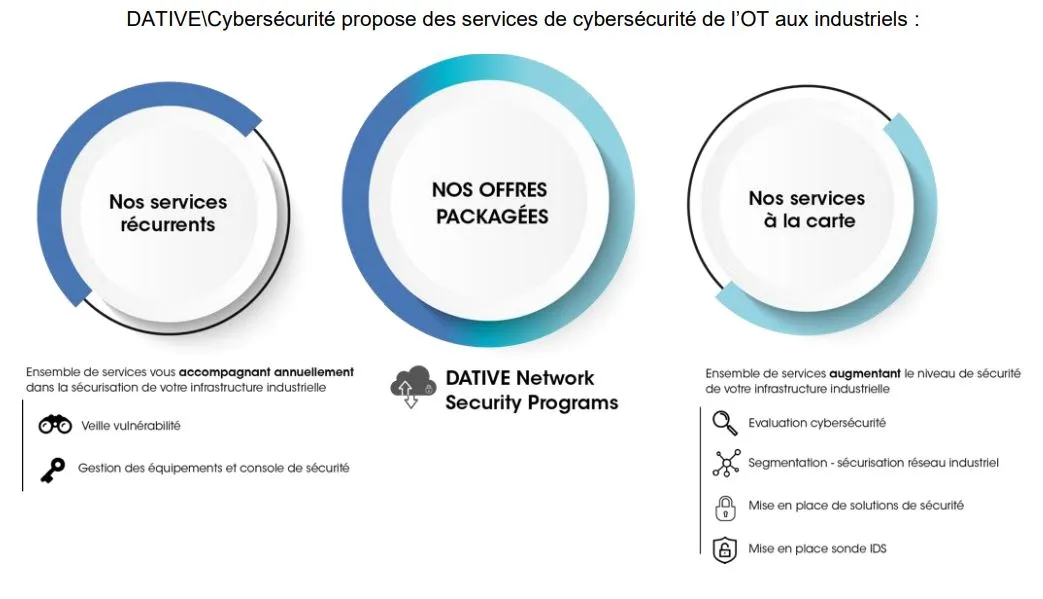
Tailored Services for a Customized Response
DATIVE offers customized services, tailored to the specificities of each industrial network, ensuring optimal long-term security. Here are a few examples:
- Cybersecurity Assessment: We conduct an in-depth risk analysis, audit infrastructures, and provide tailored recommendations to strengthen system security step by step.
- Segmentation and Securing of Industrial Networks: We implement advanced security policies to isolate critical industrial environments, preventing the spread of threats across different network segments.
- Implementation of Security Solutions: We deploy solutions such as firewalls, identity and access management (IAM) systems, endpoint sealing, white stations, and antivirus software. These industrial cybersecurity solutions are dedicated to protecting critical infrastructures.
- Integration of IDS Probes: We install intrusion detection systems (IDS) to monitor networks in real-time, providing comprehensive visibility into potential attacks and suspicious behaviors.
Recurring Services for Continuous Protection
For optimal daily security, DATIVE offers recurring services that ensure continuous monitoring and management of security equipment.
- Vulnerability Monitoring: We actively monitor vulnerabilities in our clients' equipment. These tests are conducted in a controlled environment to validate the effectiveness of solutions and ensure system non-regression.
- Security Equipment Management: We handle the management, supervision, and maintenance of security equipment (firewalls, IDS, IPS, etc.), ensuring their proper functioning and regular updates.
- Security Console Management: We centralize the management of security consoles to provide full visibility into your infrastructure's security systems. This enables a rapid and coordinated response to incidents.
Bundled offers for simplified management
DATIVE also offers turnkey solutions to simplify the management of industrial cybersecurity, tailored to the specific needs of each company.
- DATIVE Network Security Program: This comprehensive program covers the assessment, implementation, and management of industrial network security. It ensures the protection of industrial systems while maintaining their performance and availability.
- DATIVE Vulnerability Program: This program is specifically designed for proactive vulnerability management. It includes detection tools, vulnerability management processes, and corrective actions to mitigate potential risks before they become threats.
These packaged solutions offer a structured and scalable approach to cybersecurity, allowing each company to strengthen its infrastructure while simplifying the management of its security systems.
How to react in case of an industrial cyberattack?
In the event of an industrial cyberattack, speed and accuracy of actions are crucial to limit the damage. An appropriate response requires prior preparation, a good understanding of security processes, and efficient resource management to contain and resolve the situation. This section explores the best practices of industrial cybersecurity to follow in case of an attack. The goal is to ensure a quick and effective response, while preserving the integrity and availability of the industrial infrastructure.
- Disconnect the machine from the internet or the IT network
Immediately disconnect the network (Wifi and Ethernet) from an infected device to prevent the spread of the attack. This action isolates the device and minimizes the risks to other equipment connected to the infrastructure. By interrupting the network connection, the attack loses its communication vector, thus limiting its scope.
- Do not turn off the device
Keep the device powered on preserves the digital evidence needed for analysis. Turning off a device can alter crucial traces, compromising the post-incident investigation. System logs and other temporary files may be deleted if the device is powered off.
- Notify IT support
Immediately inform the IT team allows for a swift response to the incident. The team can then assess the situation, implement isolation measures, and begin the analysis. Smooth communication with IT experts ensures a coordinated and effective response.
- Do not use the device anymore
Quarantine the infected device to prevent compromising other systems. Continued use of an infected device can lead to the spread of additional malware. Isolating the device ensures that the attack does not spread to other segments of the network.
- Inform your colleagues
Quick communication with teams helps maintain vigilance and prevent further infections. Informing other departments helps limit propagation and avoid a secondary attack. Internal alerts strengthen security measures and prepare teams for immediate actions.
Conclusion
Anticipating cyberattacks is crucial to ensuring the security of your industrial infrastructures. Adopting best cybersecurity practices and investing in specialized software and equipment helps reduce risks. Integrating tailored security solutions ensures continuous protection against emerging threats. A proactive approach helps secure your systems and ensures the sustainability of your industrial operations.
Do not let vulnerabilities compromise the security of your industrial network.
Contact us for more information





