
Inventory & Mapping of Technical Equipment in a Wastewater Treatment Plant in Bretagne
A local authority located in Bretagne, operating a wastewater treatment plant made up of six treatment basins, called on DATIVE’s expertise in order to strengthen the cybersecurity of its industrial environment.
This site, largely automated and integrating heterogeneous OT equipment, is part of a modernization dynamic of public infrastructure and a transition toward Industry 4.0, with a gradual increase in connected systems and IIoT architectures.
Aware of regulatory developments and new requirements related to the NIS2 directive, the local authority needed to take a first structuring step: to obtain a reliable, comprehensive, and up-to-date view of all its industrial equipment and the associated flows.
This approach was an essential prerequisite to assess cyber risks and initiate a security program in line with ANSSI best practices and NIS2.

Cybersecurity assessment and needs expressed by this wastewater treatment plant
Before our intervention, this Breton wastewater treatment plant was facing several issues commonly found in legacy industrial environments:
Lack of visibility into the network architecture
Our client had little consolidated information on:
- The inventory of PLCs and connected equipment,
- The actual topology of the OT network,
- The communication paths between the various cabinets and systems,
- The software versions in use,
- The diversity of vendors and protocols.
Documents existed, but were partial, incomplete, or outdated.
Limited knowledge of the OT architecture and strong reliance on team memory
The transfer of information relied heavily on the internal memory of the technical teams. The local authority therefore expressed a clear need: to make knowledge more reliable, document the infrastructures, and reduce areas of uncertainty.
Cyber maturity still low, but a strong willingness to evolve
Although OT maturity was still limited, the stakeholders we met—operations managers and staff responsible for supervising the basins—were particularly engaged and eager to move toward a structured industrial cybersecurity approach.
NIS2 compliance in sight
Anticipating its future inclusion within the scope of the NIS2 directive, the site needed to:
- Have a precise and regularly updated inventory,
- Understand the interconnections between critical equipment,
- Identify sensitive areas,
- Prepare the next steps: segmentation, security audits, remote access hardening, OT monitoring…
Our intervention for this public organization: comprehensive inventory & mapping
To address these needs, DATIVE leveraged its expertise in industrial cybersecurity, relying on a proven methodology tailored to sensitive environments such as wastewater treatment plants.
Step 1 – General site walkthrough
We began with a complete visit of the facility together with the technical teams in order to:
- Understand the overall operation of the basins and the associated PLCs,
- Identify the electrical and OT cabinets,
- Locate critical areas,
- Establish an initial view of the industrial network.
This immersion is essential to correlate the future mapping with the operational reality on the ground.
Step 2 – Cabinet-by-cabinet inventory
Our team then carried out a detailed survey in each network cabinet and each OT rack. For every connected device, we collected:
- Equipment name,
- Function,
- Location,
- IP address,
- MAC address,
- Brand and model,
- Software or firmware version,
- Physical links (cables) with other equipment.
This step makes it possible to reconstruct a comprehensive and reliable inventory, a fundamental prerequisite for any OT security approach.

Technology used: passive scanners for a non-intrusive cybersecurity intervention
In order to avoid any impact on PLCs or on the industrial process, we exclusively used passive network scanners designed for sensitive environments.
This method ensures:
- Zero disruption to the OT network,
- Accurate collection of equipment and their behaviors,
- Non-intrusive detection of industrial protocols in use (Modbus, Profinet, …).
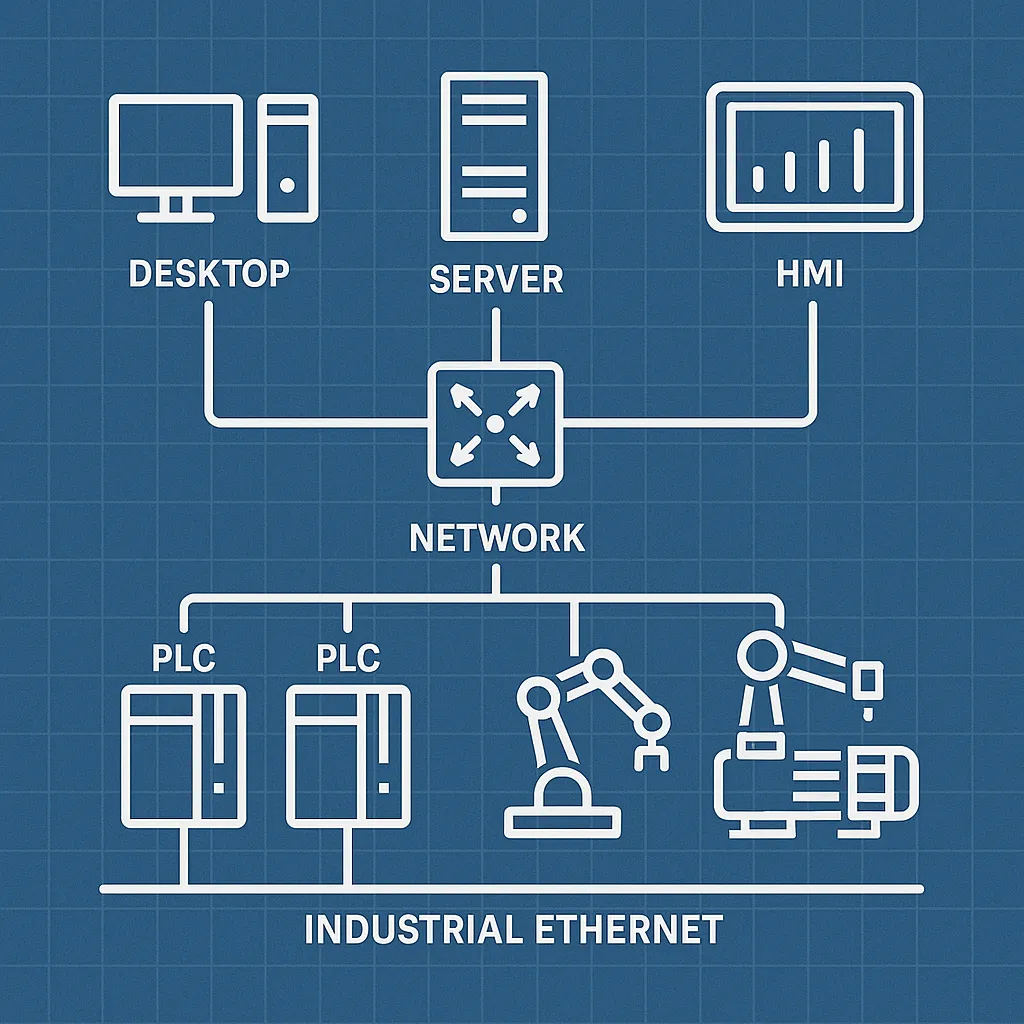
Step 3 – Building the physical and logical mapping
Back at the office, our experts consolidated all the data in order to produce two complementary views:
Physical view:
- Representation of the cabling between each cabinet
- Identification of switches, PLCs, HMIs, PCs, and network equipment
Logical view:
- Network topology
- Existing segmentation
- Potential IT/OT interactions
These two views provide a comprehensive understanding of how the industrial network operates, which is essential to prepare segmentation in line with IEC 62443 or a future deployment of industrial firewalls, bastion hosts, or OT IDS solutions.
Contact us now to discuss your environment.
Results and benefits for this local authority located in Bretagne
Thanks to DATIVE’s intervention, our client now benefits from a clear, accurate, and reliable view of its OT architecture.
Full visibility over its connected equipment
The consolidated inventory makes it possible to know exactly:
- Which equipment is present in each cabinet,
- Which PLCs communicate with each other,
- Which versions are in production.
Overall understanding of its architecture
The dual mapping (physical and logical) provides the client with:
- A structured view of how the wastewater treatment plant operates,
- Faster diagnostic capabilities in the event of an incident,
- Better control of IT/OT interconnections.
A solid foundation for a cybersecurity approach
This inventory constitutes the essential first building block to go further:
- Network segmentation (IEC 62443 zones and conduits),
- OT cybersecurity audit,
- Deployment of an industrial firewall,
- Remote access management (VPN, bastion),
- Deployment of OT monitoring or a SOC.
Contribution to NIS2 compliance
Thanks to this documentation:
- The local authority can demonstrate its proactive approach to cybersecurity,
- Critical activities are better identified,
- Future NIS2 obligations will be easier to address.
Conclusion
The intervention carried out by DATIVE at this wastewater treatment plant in Bretagne perfectly illustrates the importance of OT inventory and mapping within an industrial cybersecurity strategy.
By laying the essential foundations, our client is now ready to engage in a more advanced cybersecurity approach, thereby strengthening the resilience, service continuity, and regulatory compliance of its wastewater infrastructure.
Are you a local authority or a water operator?
If, like this client, you would like to carry out an OT inventory, obtain reliable mapping, or prepare for NIS2, DATIVE is here to support you.
Contact our experts for an initial discussion about your environment.





