
Inventory, mapping, and flow analysis for a leader in industrial pastry production
To strengthen cybersecurity and improve the reliability of its OT production network, a major agri-food player based in the Auvergne-Rhône-Alpes region called on DATIVE. The objective was to inventory connected equipment, map the industrial network, and analyze critical communications to strengthen cybersecurity and the resilience of its OT infrastructure.
An OT network essential to the operations of the food production site
A major industrial site in the Auvergne-Rhône-Alpes region where production continuity is critical
DATIVE intervened on a food production site located in the Auvergne-Rhône-Alpes region, specialized in manufacturing pastries that are frozen and distributed at large scale. The daily operation of the plant relies on several automated production lines, all connected through a single and extensive OT network made up of more than 500 industrial devices communicating over EtherNet/IP, Profinet, Modbus TCP, OPC UA, and more. In this environment, network performance and stability directly determine operational continuity and product quality.

A large, heterogeneous OT infrastructure that is difficult to fully understand
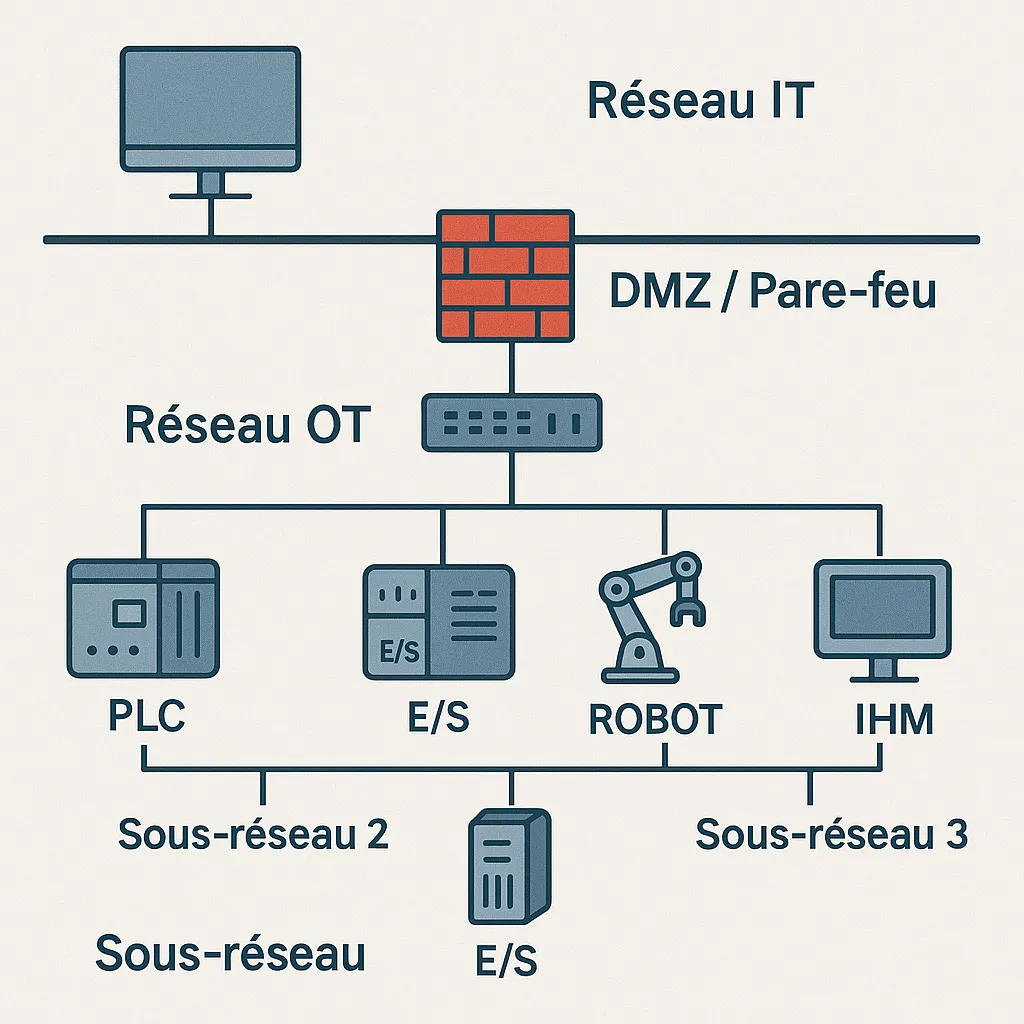
The network architecture relies on a single production VLAN deployed across the entire site. In each zone, an isolated local LAN (non-managed switches) groups together the machine’s equipment; no inter-subnet routing exists between these LANs. The production VLAN enables centralized access (supervision, maintenance, diagnostics) to every cabinet without creating lateral communications between the local LANs. This architecture, built progressively over time through extensions and line upgrades, resulted in a highly heterogeneous environment in terms of equipment and configurations. Some zones had never been documented, some devices were nearing end-of-life and end-of-support, and no consolidated view of the network existed.
This lack of visibility limited the automation and maintenance teams’ ability to quickly diagnose incidents or anticipate failures linked to obsolescence. Understanding interactions between devices was partial, making it difficult to prepare upgrades or define a coherent cybersecurity strategy.
Increasing regulatory and cybersecurity requirements in OT environments
This food production site also needed to strengthen its resilience against cyberthreats targeting industrial environments: intrusions, ransomware, network disruptions, or compromise of PLCs. These risks are highlighted by ANSSI in its recommendations on industrial control systems cybersecurity.
At the same time, the company had to anticipate the obligations of the NIS2 directive and align its practices with the IEC 62443 standard, the international reference for OT security. These frameworks require better control of assets, data flows, and technical dependencies, making reliable and exhaustive network documentation essential.
Lacking visibility over your OT equipment? DATIVE helps you build a reliable and actionable network inventory.
A network-wide understanding essential to securing pastry production operations
Understanding and documenting a complex and heterogeneous network
With no existing documentation, the site relied mainly on the operational memory of automation technicians and engineers. This dependency made network management difficult on a daily basis: inconsistent addressing, unidentified obsolete equipment, poorly documented technical zones, and subnets used with no global visibility.
The objective assigned to DATIVE was to produce a single, reliable, and comprehensive reference dataset, allowing full control and understanding of the production network.
Preventing production line downtime and ensuring this food factory’s operational continuity
Food production facilities operate under strict throughput and quality constraints. A network disruption can quickly impact production, particularly during critical phases such as freezing. The main challenges included:
- Stability of communications between PLCs and auxiliary equipment,
- Reduction of risks tied to equipment obsolescence,
- Control of exchanges between subnets within the production VLAN,
- Identification of network paths likely to cause incidents.
Aligning the CISO, automation teams, and IT around a shared understanding
Our mission involved the Corporate CISO, responsible for the group’s cybersecurity strategy, the automation engineer in charge of OT installations, and the IT team managing the overall IT infrastructure. One of the main goals was to establish a common language across these roles by providing precise, structured, and accessible documentation.

Need a structured OT assessment? DATIVE consolidates your data and builds a unified IT/OT documentation base.
A structured methodology: inventory, mapping, and flow analysis
Inventorying and qualifying all equipment within the industrial client's OT network
DATIVE’s cybersecurity experts conducted a complete OT inventory by physically inspecting each cabinet on the site. This hands-on approach enabled precise identification of all PLCs, sensors, HMIs, industrial workstations, switches, and gateways. More than 500 devices were documented at a high level of detail: IP addressing, production role, software versions, end-of-maintenance, and end-of-life status.
This dataset now serves as the site's operational reference, essential for anticipating obsolescence and planning network evolution.
Mapping the physical and logical structure of the network
The network mapping was carried out by combining field observations with the deployment of an IDS probe in a central cabinet. The analysis made it possible to reconstruct the actual links between cabinets, racks, and equipment, while confirming interconnections within the production VLAN and identifying the subnets in use.
This food production site now benefits from:
- A per-room and per-cabinet network map,
- A global view of the OT network,
- A simplified diagram of key interconnections.
Analyzing flows to understand critical communications
Our cybersecurity engineers performed an in-depth analysis of traffic flows within the production VLAN using the IDS probe and passive analysis tools. A detailed flow matrix enabled identification of:
- Critical communications between devices,
- Protocols in use,
- Active ports and bandwidth usage,
- Broadcast traffic potentially generating disturbances.
Beyond the technical findings, this approach provides essential visibility to strengthen network stability, adjust device configurations, or prepare segmentation projects aimed at isolating critical systems. Additionally, implementing continuous flow monitoring allows teams to track traffic evolution over time and detect anomalies or unexpected behaviors more easily.
Thanks to this analysis, the site now has a structured understanding of its OT communications, helping support decision-making, plan network optimization, and prepare for compliance with NIS2 and IEC 62443 requirements.

Want to understand and control your OT flows? DATIVE performs passive analyses tailored to sensitive industrial environments.
Strong foundations to improve OT performance and cybersecurity
Following DATIVE’s intervention, the factory now has complete and up-to-date visibility of its OT infrastructure, consolidated in a single reference including inventory, mapping, and flow analysis. This factual foundation reduces the risk of production downtime, enhances system resilience and availability, and establishes a common working framework for OT and IT teams, supporting better coordination and faster decision-making. It also facilitates progressive compliance with NIS2 and IEC 62443, while preparing future segmentation and monitoring initiatives. The result is a better-documented, clearer, and easier-to-administer OT network, contributing directly to business continuity and long-term stability.
Accelerate your industrial cybersecurity with DATIVE
Mastering your OT network is a long-term effort. Beyond one-time interventions, DATIVE helps you establish a sustainable operational foundation: reliable inventory, actionable network mapping, regular flow analysis, segmentation planning, monitoring adapted to production constraints, and a continuously updated documentation framework.
DATIVE then supports you end-to-end in operational cybersecurity: configuration adjustments, segmentation deployment and validation, hardening of industrial devices and workstations, integration with monitoring and logging tools, implementation of continuous supervision, change management, vulnerability monitoring and remediation, and scheduled MCO/MCS activities. The goal: reduce the risk of downtime, stabilize operations, improve availability, and give OT/IT teams a shared reference to make decisions quickly and effectively.
Tell us about your site. In 30 minutes, our OT cybersecurity experts assess your challenges and propose the most relevant first step to secure and sustain your OT infrastructure.





