
Client case study: Comprehensive OT diagnosis and cybersecurity audit for a drinking water operator
In the French Alps, DATIVE supported an inter-municipal authority by delivering a comprehensive OT diagnosis to restore visibility over industrial infrastructures, secure an essential public service, and prepare for NIS2 compliance.
In the French Alps, we supported an inter-municipal authority responsible for water management, ensuring an essential public service: pumping, treatment, wastewater purification, and drinking water distribution. This activity relies on critical industrial infrastructures whose availability must be guaranteed at all times.
While the IT environment already benefited from solid foundations, the industrial side presented a very different situation. There was no network inventory, no OT network mapping, and no structured OT cybersecurity approach in place. In the context of compliance with the NIS2 directive, it became essential to understand the actual state of the installations before considering any security measures. It was in this context that we carried out a comprehensive OT diagnosis, combining inventory, network mapping, and industrial cybersecurity auditing.

An Alpine territory dependent on critical water infrastructures
The scope of intervention covered around ten industrial sites spread across an Alpine territory. Pumping stations, electrical rooms, control rooms, wells, and a wastewater treatment plant form a heterogeneous yet highly interdependent system. Some sites are modest in size, while others rely on more complex architectures with several dozen interconnected industrial devices.
From an IT perspective, structured measures were already in place: VLANs, crisis management procedures, business continuity plans, and disaster recovery plans.
On the OT side, however, the assessment was clear. The industrial network operated flat, with no equipment inventory, no OT network mapping, and no segmentation. Industrial cybersecurity had never been addressed in a structured way due to a lack of visibility and dedicated expertise. This situation directly exposed a critical infrastructure linked to water management to cyber risks, within an increasingly demanding regulatory context.
A clear priority: restoring visibility to secure a vital public service
In the water sector, service continuity is non-negotiable.
A pump shutdown, an inaccessible PLC, or unavailable supervision can quickly lead to supply interruptions or environmental risks. The challenge was therefore clear: strengthen OT security without ever compromising operations.
Without network visibility, no prioritization was possible. Before any technical action, we needed to answer fundamental questions:
- which devices are actually connected to the network?
- where are they located?
- how do they communicate with each other?
Network inventory and OT mapping therefore formed the essential foundation for building a coherent strategy, compatible with both field constraints and NIS2 compliance requirements.

The DATIVE approach: rebuilding the real picture of the OT network
To address these challenges, we adopted a progressive, pragmatic, and field-oriented approach. Our objective was not to abruptly transform the existing setup, but to reveal the true state of the industrial network so that the client could make informed decisions and act with full awareness.
OT inventory: 200 devices documented across 10 sites
We physically inspected electrical cabinets and technical rooms at each site. Every IP-connected OT device was identified and documented: IP and MAC addresses, network membership, vendor, model, functional role, and precise location.
Cable tracing work made it possible to understand physical connections, which were often completely undocumented.
In total, approximately 200 OT devices were inventoried, providing for the first time a comprehensive and factual view of the industrial asset base.
Physical and logical mapping: reconstructing the OT puzzle
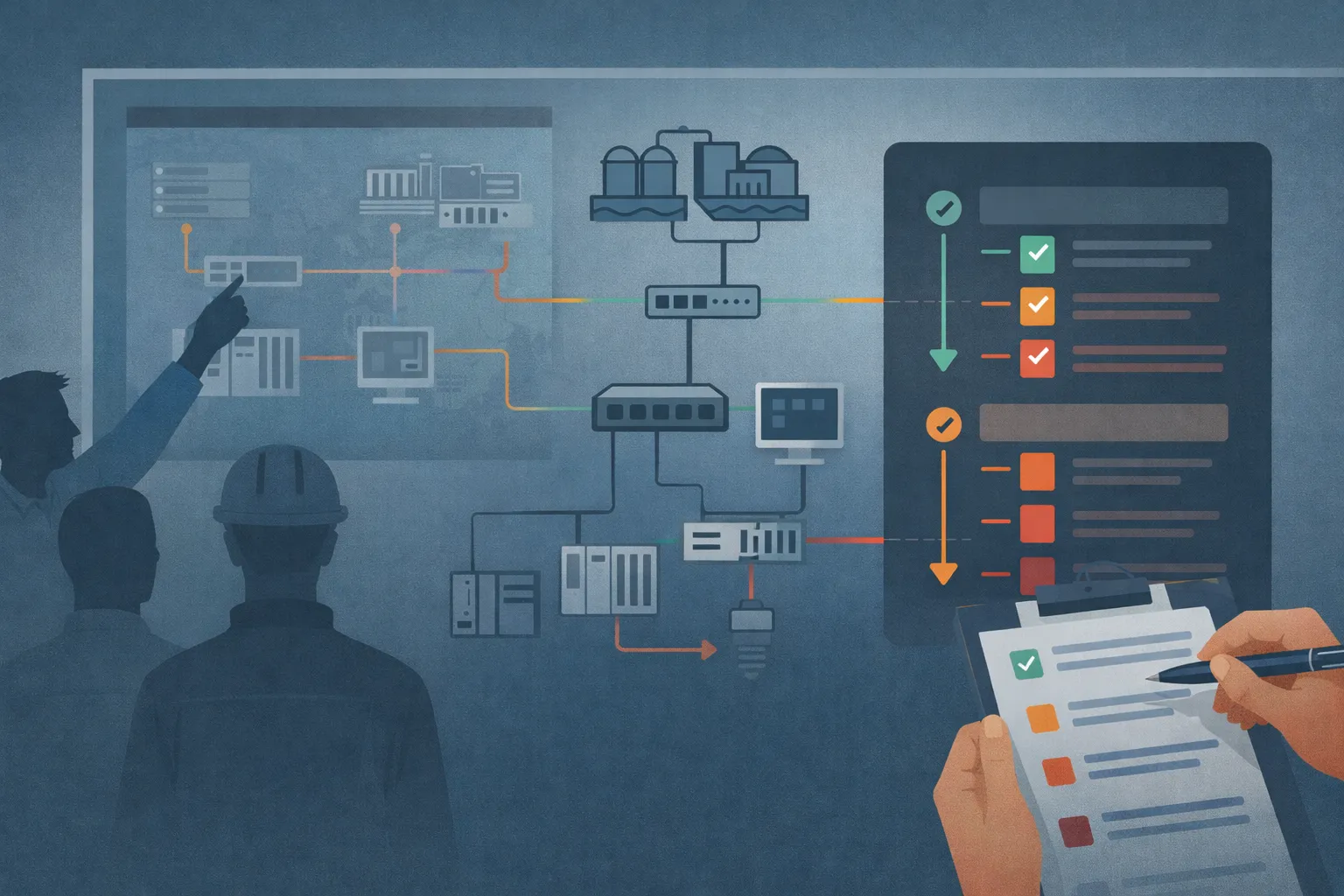
Based on this inventory, we produced complete OT maps, both physical and logical.
Physical mapping makes it possible to visualize each device in its real environment: cabinet, room, site, and interconnections. Logical mapping highlights network organization, existing VLANs, and functional relationships between industrial systems.
This dual representation provides a global understanding of the architecture and immediately reveals critical dependencies and areas of weakness.
Truly understand your OT network: DATIVE delivers actionable physical and logical mappings to identify weak points and structure your security decisions.
Flow analysis using an IDS probe: understanding real behaviors
To complete this picture, we deployed an IDS probe at the core of the OT network. This dynamic analysis made it possible to observe the actual flows exchanged between devices and supervision systems.
The objective was simple: understand before acting.
Identifying communications essential to operations, distinguishing secondary flows, and detecting risky behaviors. This step provided a factual view of real network usage, often very different from initial assumptions.
OT cybersecurity audit: assessing maturity and defining an action plan
Based on field observations, mappings, and flow analysis, we conducted an OT cybersecurity audit grounded in recognized frameworks such as ANSSI guide, NIST framework, and CIS controls.
This assessment identified structural weaknesses, evaluated OT cybersecurity maturity, and defined realistic priorities. The final deliverable provides a structured action plan, broken down into short-, medium-, and long-term actions, fully compatible with service continuity requirements.
A structured cybersecurity assessment to define an action plan
At the end of the engagement, the client now benefits from a clear and shared reference framework. Network inventory, OT mapping, and the industrial cybersecurity audit transformed an opaque infrastructure into a readable and controlled environment.
IT teams now better understand OT constraints, field teams rely on reliable documentation, and management can steer the increase in industrial cybersecurity maturity with a long-term vision. The path toward NIS2 compliance is defined, prioritized, and aligned with operational realities.
Immediate results: full visibility and a controlled security strategy
This project illustrates a situation that remains common: OT networks that have historically functioned, but are poorly documented and insufficiently secured. By restoring visibility, we enabled our client to regain control of its industrial infrastructure.
The benefits are tangible:
- a comprehensive understanding of the OT asset base,
- stronger collaboration between IT and operations,
- reduced risks linked to unknown areas,
- a new ability to plan OT network security without endangering production.
Regain control of your OT network. DATIVE provides the visibility needed to reduce risk, align IT and operations, and deploy a controlled security strategy without impacting production.
Conclusion: a necessary foundation to secure water industrial infrastructures
In the water management sector, industrial cybersecurity starts with knowledge. This OT diagnosis laid the essential foundations for any sustainable security approach: visibility, understanding, and prioritization.
At DATIVE, we support industrial operators at every stage of this transformation, from the initial OT audit to advanced security of critical infrastructures.
Looking to assess the security of your industrial installations? Our teams are available to discuss your OT challenges.





