
Defense in depth: a nuclear safety principle that has become a pillar of industrial cybersecurity
Developed in the field of nuclear safety to prevent major accidents, defense in depth is now a fundamental concept in industrial cybersecurity. It is based on the idea of successive layers of protection, applied to critical environments, to ensure resilience, security, and business continuity.
Why defense in depth has become essential in industrial cybersecurity
Cyber threats are increasingly weighing on OT processes
Digital transformation is disrupting industrial environments. The growing interconnection between IT and OT systems is creating an unprecedented attack surface. What used to be isolated networks protected by obscurity is now exposed to the same threats as traditional IT.
- Concrete example: the integration of remote maintenance solutions or IoT sensors increases the number of entry points for cyber attackers.
- Consequence: a simple piece of malware introduced via a desktop PC can spread to the controllers and disrupt a production line.
Energy, water, transportation, healthcare: why is implementing a defense-in-depth approach vital for your industrial infrastructure ?
Industrial sectors are not just businesses: they form the backbone of services that are essential to society.
- Energy : An attack on an electrical grid can cause massive power outages, as seen in Ukraine in 2015.
- Water : malicious tampering with pumping or treatment equipment can endanger public health.
- Transportation : interruptions in signaling or control systems can paralyze an entire region.
- Health : the availability of hospital systems and pharmaceutical production is vital.

Your industrial systems, often designed without native security, require OT security measures.
Historically, industrial systems (SCADA, DCS, programmable logic controllers) were designed to last for decades in supposedly isolated environments. Their priority was availability and reliability, not security.
- Communication protocols (Modbus, Profibus, OPC DA, etc.) were often designed without encryption or authentication.
- Software updates are rare, as any production downtime can have serious consequences.
- Supervision solutions (HMI, SCADA) sometimes still run on obsolete operating systems.
Consequence : these systems constitute vulnerable areas that require special security measures.
Cyber failure in industry: consequences ranging from production stoppages to human risks
A cyberattack on an OT environment not only causes IT disruption, it can also have very real impacts :
- Production stoppage : direct financial losses and disruption to the supply chain.
- Environmental risks : toxic waste, accidental pollution.
- Human consequences : exposure of workers to physical hazards, endangering populations if critical infrastructure is affected.
Don't leave your industrial environments exposed to invisible threats. Defense in depth is your best guarantee against the unpredictable.
Implementing a defense-in-depth strategy for your factories and industrial environments
A multi-layered model to limit the consequences in the event of an attack
Defense in depth is based on a simple principle: don't rely on a single security barrier, but rather layer several complementary layers on top of each other. This approach, inherited from nuclear safety, is now essential in the connected industry.
The idea is not to pile on technologies, but to design a coherent protection architecture where each layer slows down the attacker, limits their progress, and increases the chances of detection. This is precisely what DATIVE applies in its support services: starting with the mapping of industrial assets, analyzing IT/OT flows, then building a progressive security strategy adapted to operational constraints.

La complémentarité des protections
In an industrial environment, no technology is foolproof. A poorly configured firewall, outdated antivirus software, or overly permissive access policies can open the door to compromise. That's why complementary layers are essential: each barrier compensates for the limitations of the others.
At DATIVE, we favor a comprehensive approach by seamlessly integrating a variety of solutions: network segmentation, OT detection probes, identity management, and real-time monitoring. Effectiveness comes from the synergy between protections, not simply their juxtaposition.
Tell us about your needs and let's work together to build a customized defense strategy.
A balance between technology, organization, and people
Defense in depth is not just about tools. It relies on a balance between three dimensions :
- Technology : protection and monitoring solutions.
- Organizational : clear procedures and a continuity plan.
- Human resources : training and awareness-raising for teams.
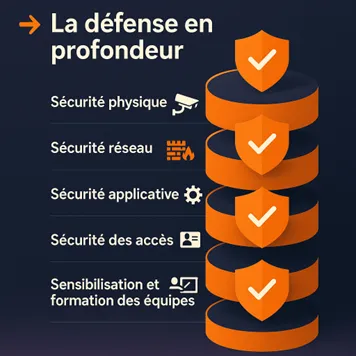
Security layers in defense in depth
Physical security
The first barrier is often the most tangible: preventing unauthorized access to infrastructure. Access controls using badges, cameras, surveillance of sensitive areas, and partitioning of server rooms form the basis of robust security.
In its audits, DATIVE always includes an assessment of physical security measures to ensure that protection begins as soon as individuals enter the site.
IT/OT network security
The separation between IT and OT networks is fundamental. Strict segmentation, the creation of DMZ zones, the deployment of industrial firewalls, and probes adapted to OT protocols make it possible to limit an attacker's lateral movements.
Our DATIVE cybersecurity engineers implement architectures that comply with standards (IEC 62443, NIS2), guaranteeing our customers protected industrial environments that are monitored continuously.
Application security
Supervisory systems (SCADA, HMI, DCS) must be hardened and maintained: update management, removal of unnecessary services, continuous monitoring of logs and abnormal behavior.
Access and identity security
Users and their access rights represent another critical link. Multi-factor authentication, strict privilege management, and adoption of a Zero Trust approach are essential levers.
Our DATIVE cyber experts deploy identity management (IAM) solutions tailored to OT environments, providing granular control over who can access what, and under what conditions.
Awareness raising and training for teams
Finally, the human factor remains essential: even the best technical and organizational protections can be circumvented if users are not made aware of the issues. In an industrial environment, where the priority for teams remains production and operational safety, cybersecurity can sometimes appear to be a secondary concern.
However, attackers regularly target this human link :
- Through phishing or spear-phishing campaigns,
- By taking advantage of risky habits (sharing passwords, using uncontrolled removable media),
- Or by exploiting a lack of vigilance in the face of abnormal system behavior.
Training operators, technicians, and engineers therefore means giving them the tools to recognize threats, respond effectively, and quickly report any suspicious incidents.
We deliver these training courses in a manner tailored to the realities on the ground :
- Practical scenario (simulation of an incident or targeted attack),
- Regular crisis management exercises,
- Developing a genuine shared safety culture, where everyone understands their role in protecting the plant.
By turning employees into cybersecurity actors, defense in depth gains an extra dimension: each individual becomes an additional barrier against threats.
The benefits of defense in depth for OT environments
Risk reduction and attack surface reduction
By layering multiple layers of security, defense in depth acts as a successive filter that significantly reduces the opportunities available to attackers. Each additional barrier, whether technical, organizational, or human, helps to close a potential entry point.
In your industrial environment, this means that programmable logic controllers, SCADA systems, or field equipment are never directly exposed, but protected by a series of intermediate controls.
Let's take the example of an intrusion attempt via a remote maintenance connection :
- The first barrier (strong authentication) prevents the majority of unauthorized access,
- The second (network segmentation) limits the scope of a compromised account,
- The third (continuous monitoring) quickly detects abnormal activity.
By applying this logic, the risk of an attack reaching the operational heart of the plant is greatly reduced.
Faster intrusion detection and response
The proliferation of defense layers is not only used to block attacks. It also improves detection. When an anomaly occurs, it is spotted by one of the layers before it becomes critical.
For example, malware may go unnoticed on a monitoring station, but be detected at the network level by an OT probe or reported by a SOC through correlation of suspicious events.
This early detection is essential for:
- Limit the impact on production,
- Trigger a rapid response before the attack spreads,
- Keep financial and operational costs under control.
Resilience in the face of incidents
Even the best-protected systems are not immune to failure or successful attack. The strength of defense in depth lies in its ability to maintain a residual level of protection that prevents the worst from happening.
- If a firewall is bypassed, network segmentation will slow down the spread.
- If a user account is compromised, strict privilege management will limit the damage.
- If an automated system is targeted, monitoring will enable the affected area to be quickly isolated.
This resilience is what differentiates a company that suffers a total breakdown from an organization that manages to maintain an acceptable level of activity, even in a crisis situation. In OT environments, where availability is an absolute imperative, resilience is as much a competitive advantage as it is a regulatory requirement.
Conclusion
Defense in depth originated in the highly sensitive context of nuclear safety, where no margin for error could be tolerated. Today, this model is becoming the obvious choice for industrial cybersecurity. OT environments, which are increasingly interconnected and critical to our societies, require a multi-layered approach combining technical, organizational, and human factors.
In a world where cyber threats are constant, defense in depth is no longer an option: it is the foundation of industrial resilience.
Would you like our team to assist you in implementing a defense-in-depth strategy for your OT environments ?
Contact us now to discuss this with our experts.





