
The Zero Trust Model: An Essential Strategy in OT Cybersecurity
The Zero Trust model has become a key cybersecurity strategy for OT. This article presents its principles, its benefits for industrial cybersecurity, and the key steps to deploy a Zero Trust architecture adapted to OT network security.
What is the Zero Trust model
Principle and operation of the Zero Trust model
The Zero Trust model is a cybersecurity approach based on a simple principle: never trust by default.
Each user, device, application, and transaction must be continuously verified before accessing your industry's information system (IS).
With the rise of remote work, Bring Your Own Device (BYOD), and the spread of hybrid services, the Zero Trust model has become essential to effectively protect your IT and OT environments.
The fundamental principles of Zero Trust for IT
Its core technical principles include:
- Continuous user and access evaluation: each request is dynamically analyzed to verify the identity of the subject (operator, user, external actor, etc.) and their legitimacy to access the resource.
- Context awareness: device security state, connection location, and other parameters are evaluated to adjust access rights in real time.
- Resource sensitivity: the criticality of a resource in terms of availability, integrity, and confidentiality influences the level of control applied.
- Systematic authentication: no connection is authorized without prior verification, even for internal users.
- Principle of least privilege: each operator only has the rights strictly necessary to perform their tasks.
- Micro-segmentation and isolation: the network is divided into segments to limit the spread of potential intrusions.
Zero Trust is not a single product or a miracle technology. It is a strategic security model that must be deployed gradually. A rushed or poorly managed adoption can weaken the information system and create a false sense of security. That’s why DATIVE experts support you with a step-by-step deployment, taking into account the specificities of your factories.
The benefits of Zero Trust for industrial cybersecurity
Reducing attack surfaces
In an industrial environment, the attack surface refers to all possible entry points for a cyberattacker.
It includes your critical industrial systems, IoT sensors, OT servers, and IT/OT gateways.

With the rise of external connections, remote maintenance, industrial cloud, BYOD, and IT/OT interconnection, this attack surface has expanded significantly.
Each unsecured access point becomes a potential vector for intrusions, ransomware, or targeted sabotage.
The industrial Zero Trust model helps reduce this exposure. By applying strict and continuous access control and following the fundamental principles mentioned above, it limits unauthorized interactions with critical systems and restricts the spread of potential intrusions.
Securing access to OT systems
In an industrial site, access control to industrial control systems (ICS) must be strict and precise.
The principle of least privilege means assigning each user only the rights necessary to perform their tasks. Thus, an operator cannot perform administrative tasks or access functions beyond their responsibilities.
This strict control reduces exposure to intrusion risks. It prevents a malicious user—whether external or internal—from compromising the normal operation of industrial systems.
User control and traceability
In an OT environment, it is essential to know who accesses which resources and when.
User traceability makes it possible to monitor all actions carried out on your industrial control systems and critical infrastructures.
Implementing a traceability system serves several essential objectives:
- Event logging to detect security incidents: each connection, command, and modification is recorded to quickly detect abnormal or suspicious activities.
- Post-incident investigation: in case of an incident, logs allow reconstructing user actions and understanding the origin and extent of the incident.
- Compromise detection: traceability helps analyze flows and logs to identify any compromise or intrusion within the system.
- Logging for each information system: every critical OT system component — servers, gateways, HMI interfaces — must generate structured, centralized logs to ensure complete environmental coverage.
These technical goals ensure complete visibility over access and activity, strengthening OT network security and enabling effective incident response.
How to deploy a Zero Trust architecture?
1. Asset inventory and flow mapping
Deploying a Zero Trust architecture in an industrial environment starts with a comprehensive understanding of the perimeter to be protected.
It is strongly discouraged to secure a site without identifying its assets (PLCs, HMIs, drives, switches, etc.), understanding its architecture, and analyzing its communications.
At DATIVE, we support our clients through this critical first step.
We perform a detailed inventory of the assets present on the site: industrial control systems, PLCs, servers, workstations, sensors, and network devices.
This inventory is complemented by a mapping of physical and logical flows, providing full visibility of all communications within the industrial network.
This mapping highlights critical areas, system vulnerabilities, flat network structures, and sometimes forgotten equipment — in contexts where operational continuity often takes precedence over integrating new cybersecurity practices.
It serves as a solid foundation for building an adapted, gradual, and realistic Zero Trust strategy.
Would you like to initiate the deployment of a Zero Trust architecture within your organization? Contact our DATIVE experts for structured support tailored to your industrial challenges.
2. Network segmentation (IT / OT)
The evolution of industrial environments increases risks. The growing interconnection between IT and OT assets, the use of cloud solutions for production, and the implementation of remote maintenance services expose industrial networks to new threats.
Through rigorous segmentation, an intrusion remains confined to the zone where it occurred, thus limiting its impact on overall operations.
The Purdue model is a widely used reference for structuring industrial networks. It divides the ICS architecture into six distinct levels (Cell, Process Control, Supervision, Site-level and Industrial Perimeter Network, and Enterprise Networks) that contain IT and OT systems, illustrating how typical industrial elements interconnect. When properly deployed, it ensures complete segregation between ICS/OT and IT, allowing strict access control without disrupting operations.
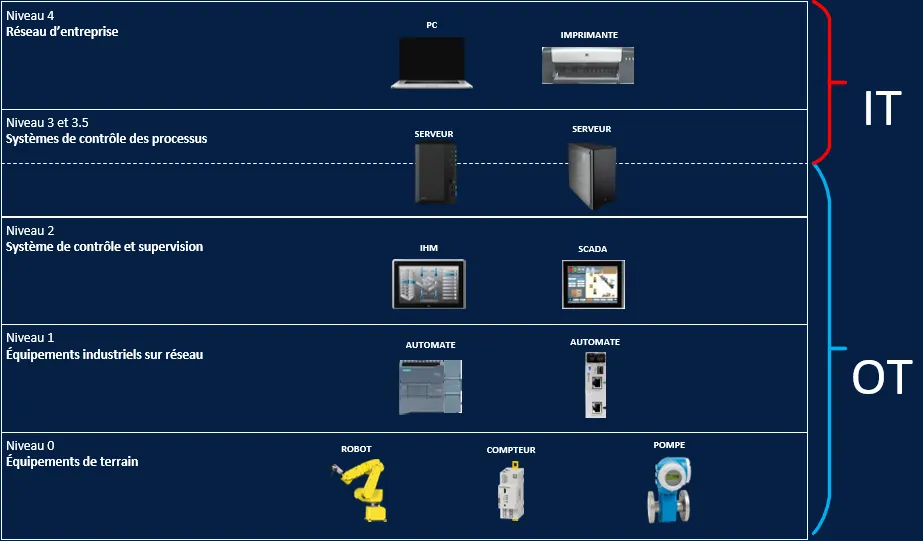
At DATIVE, we help our clients design and implement this segmentation at the core of their industrial architectures. This involves deploying industrial firewalls, Layer 3 switches to create and manage VLANs, and organizing the network logically to fit site-specific needs.
3. Strong authentication and identity management
The central principle of the Zero Trust model is that every user, device, and application must be authenticated before accessing resources — even from within the network.
DATIVE offers personalized support for implementing centralized identity management and strong authentication adapted to OT.
This approach combines:
- Multi-factor authentication (MFA): to ensure the user truly is who they claim to be.
- Rights and role management: assigning privileges strictly necessary to each role (maintenance manager, operator, external technician, etc.) following the principle of least privilege.
- IT/OT integration: authentication covers both traditional IT systems and industrial equipment, ensuring comprehensive and consistent visibility.
- Access monitoring and auditing: each connection is logged to quickly detect suspicious attempts and allow post-incident investigation.
This approach strengthens OT network security, reduces risks from compromised accounts, and prepares the organization for an efficient, controlled Zero Trust deployment.
4. Monitoring, detection, and incident response
In industrial environments, it is not enough to segment the network and control access: it is crucial to continuously monitor activities to detect any anomaly or intrusion attempt quickly.
To effectively secure an OT network, several approaches are combined:
- Event collection and correlation: logs from PLCs, SCADA, HMI, servers, and network devices are centralized and analyzed to identify unusual behavior.
- Real-time detection: specialized tools immediately flag suspicious activity, enabling a fast response before the incident spreads.
- Alert management and automated responses: in case of anomalies, automated actions can isolate the affected zone or reduce production impact.
- Audits and investigations: all activities are recorded to trace incident origins, understand attack vectors, and improve prevention measures.
These measures strengthen OT network security, limit attack impact, and improve responsiveness to threats, while ensuring continuity of industrial operations.
To implement monitoring and incident response adapted to your industrial systems, contact our DATIVE experts.
Challenges of implementing the Zero Trust model
Integration in legacy OT environments
Existing industrial infrastructures often include legacy systems (supervision stations under Windows XP, sensitive PLC configurations, etc.) that were not designed for modern cybersecurity.

Integrating the Zero Trust model into such environments requires combining modernization and gradual adaptation to avoid disrupting production continuity.
Complexity of IT and OT architectures
Modern industrial sites combine interconnected IT and OT systems, sometimes including cloud services.
This hybridization makes Zero Trust implementation more complex, as it involves managing multiple data flows and maintaining full network visibility.
Cost and change management
The transition to a Zero Trust architecture involves hardware, software, and human investments. It also requires staff training and change management to adopt new security practices while maintaining operational continuity.
Contact DATIVE today to benefit from customized support and start deploying your industrial Zero Trust architecture.
Links between standards and the Zero Trust model
The Zero Trust model fits within the European and French regulatory and normative framework that governs industrial cybersecurity. Its adoption strengthens OT system security while facilitating compliance.
- NIS2 Directive: this directive requires critical European infrastructures to strengthen cybersecurity. Zero Trust principles — such as strict access control and network segmentation — directly meet these requirements.
- LPM (French Military Programming Law): for France’s vital operators, Zero Trust complements the LPM by securing critical systems and limiting access to verified entities only.
- ISO/IEC 62443: this international standard for industrial systems defines best security practices. Zero Trust applies them through micro-segmentation, strong authentication, and continuous access monitoring.
In practice, the Zero Trust model provides an operational framework that strengthens OT cybersecurity while helping meet regulatory obligations and recognized best practices.
To secure your industrial systems and align with French and European standards and directives through a Zero Trust approach, contact our DATIVE experts.
Conclusion
Today, the Zero Trust model is an essential lever for securing industrial systems and reducing risks related to OT environments. However, its implementation can be complex: legacy systems, hybrid architectures, and production continuity requirements make each deployment unique.





