
4 Examples of Industrial Cybersecurity Attacks
Industrial cybersecurity attacks are no longer fiction or rare exceptions. From attempted poisoning to power outages, safety system overrides, and global ransomware paralysis, real-world OT attacks are on the rise. These incidents expose critical vulnerabilities in industrial environments and underscore a crucial reality: operational systems have become high-value strategic targets.
Why document OT attacks?
A real but underreported threat
Industrial cybersecurity is now a strategic issue. Yet it is often pushed to the background, perceived as a technical subject, poorly visible and misunderstood outside specialized circles.
An industrial cybersecurity attack is not limited to production downtime. It can compromise an essential service, physically damage equipment, or expose operators to real risks. OT systems are now high-value targets, and their compromise has tangible, lasting, and systemic consequences.
Attacks like Stuxnet, Triton, or Industroyer have made history, but they are only the visible part of a global phenomenon. Examples of OT attacks are multiplying, including in environments considered closed or low-risk.
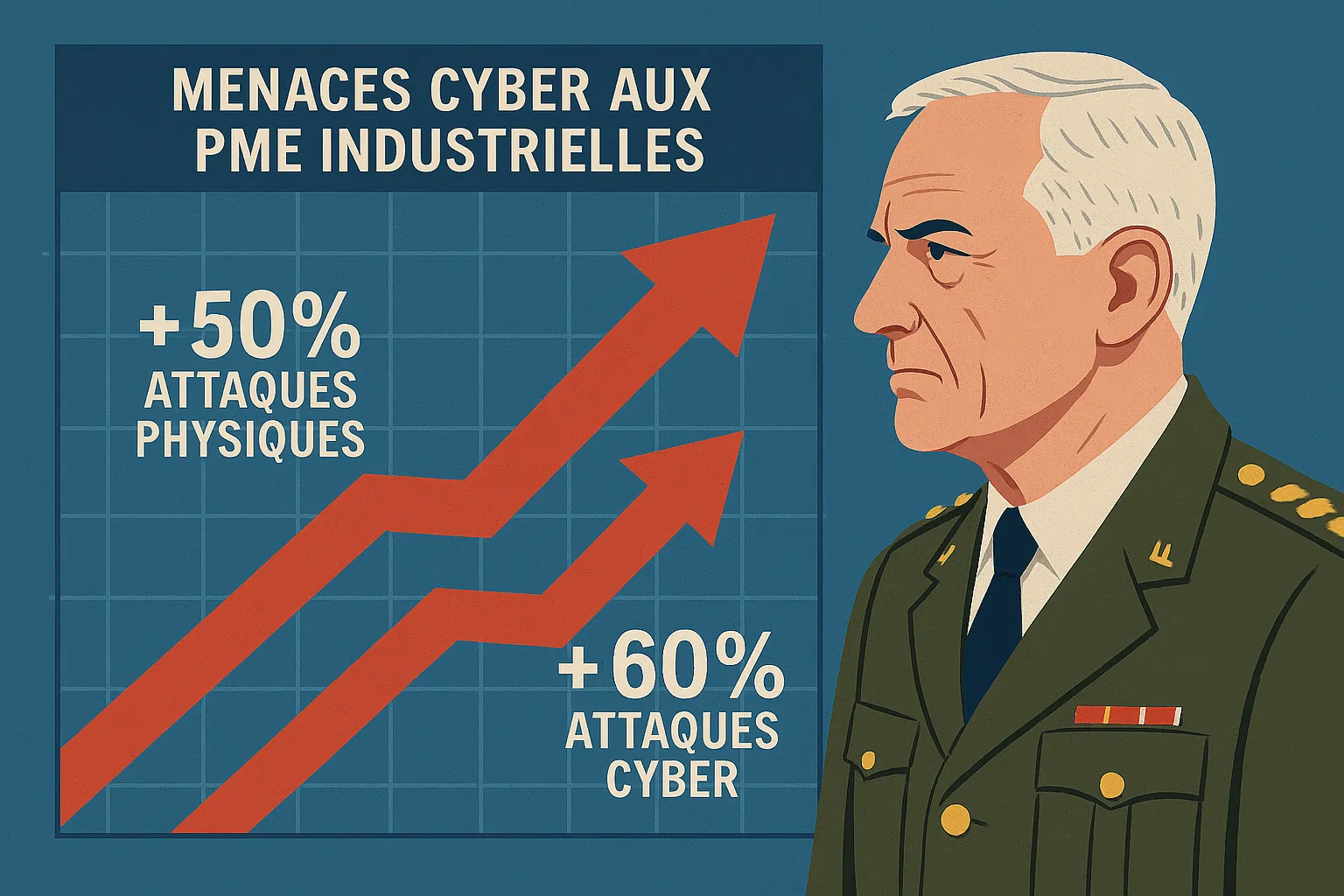
This reality is confirmed by General Philippe Susnjara (DRSD), who warns about the surge in threats against strategic industrial SMEs. In one year, these organizations have seen a +50% increase in physical attacks and +60% increase in cyber attacks. These companies, sometimes holding critical technologies but often under-equipped in terms of security, have become prime targets for attackers.
“The enemy now targets our weak links rather than our fortresses.” General Philippe Susnjara, DRSD
In this context, industrial resilience can no longer focus only on the most visible areas. It requires comprehensive security: technical, human, and organizational.
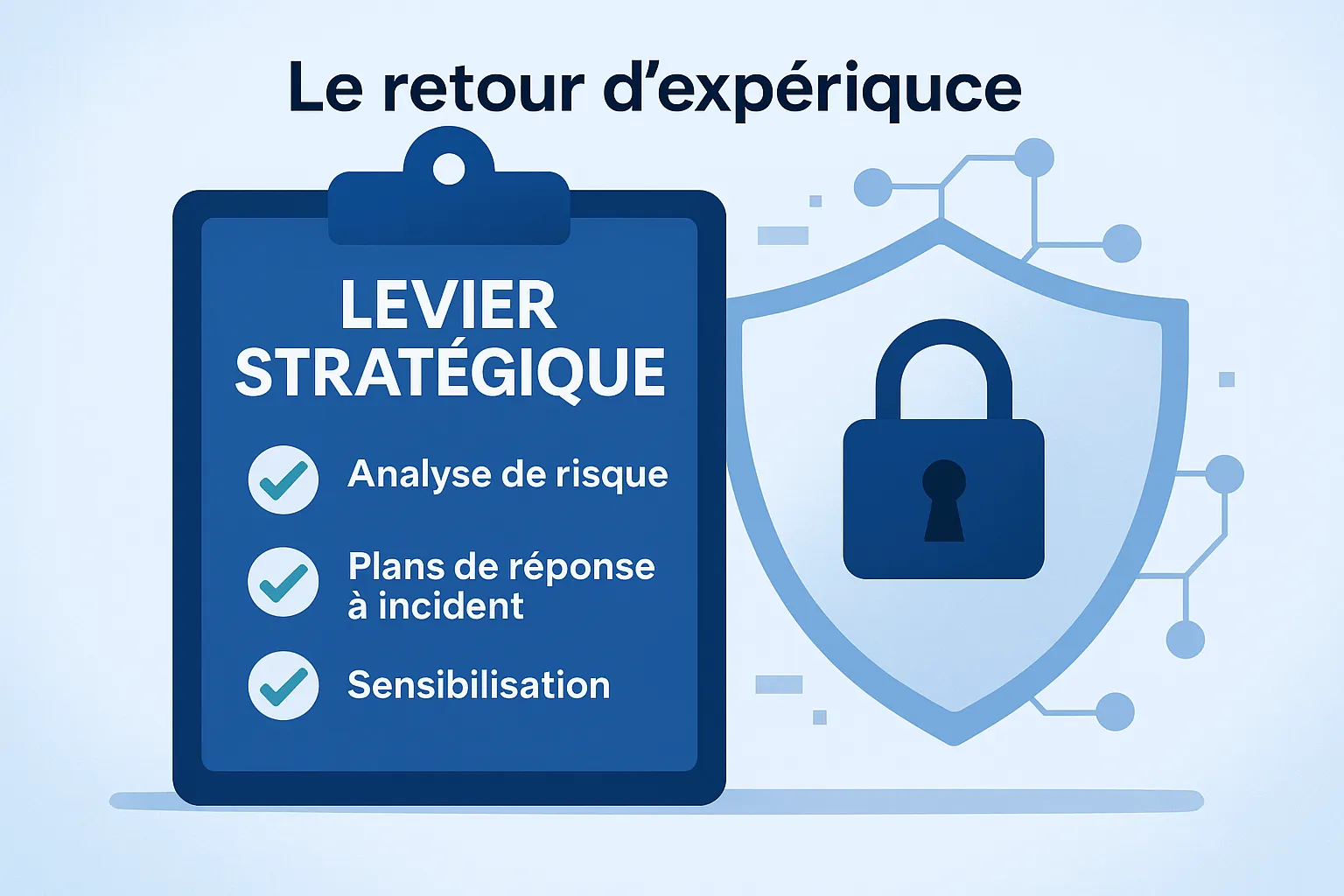
The value of feedback in building resilience
Each incident is a learning opportunity. But it must be documented, analyzed, and turned into lessons learned. Cybersecurity feedback is still underutilized in industry, with direct consequences on organizational maturity.
This shortfall results in two critical effects:
- On one hand, it slows internal progress. Without formal documentation, teams change, incidents repeat, and mistakes recur. The company remains stuck in a reactive approach, unable to build a robust long-term defense.
- On the other hand, it isolates the company from its ecosystem. Without structured sharing, feedback benefits no one. It becomes impossible to detect emerging trends or to collectively prepare for new attack vectors.
Feedback should not be viewed as a burden. It is a strategic lever: it feeds risk analysis, structures incident response plans, supports OT team awareness, and enables concrete alignment with regulatory requirements.
Preparing for audits and meeting regulatory requirements
In an increasingly regulated environment, experience feedback becomes a key element of compliance.
Frameworks such as NIS2, the French Military Programming Law, ISO/IEC 27001, or IEC 62443 require industrial players to demonstrate their ability to:
- detect threats,
- respond quickly and effectively,
- trace corrective actions taken,
- continuously improve their security posture.
Well-structured experience feedback directly supports these requirements. It provides visibility on the actions taken, justifies technical and organizational decisions, facilitates audits, and reinforces trust from both partners and authorities.
In short, formalizing incidents and capitalizing on every attack means transforming a past vulnerability into a lever for credibility, maturity, and resilience.
To better understand the challenges and adopt the right reflexes, let’s now explore four concrete examples of industrial cybersecurity attacks, rich in lessons for preparation and effective response.
Attack Example #1: Attempted Water Poisoning in Oldsmar (Florida, 2021)
Context and vector
On February 5, 2021, an unknown attacker remotely accessed an OT supervision station at a water treatment plant in Oldsmar, Florida, which supplies around 15,000 residents.
Access was gained via TeamViewer, a remote access tool installed on the workstation and poorly secured: weak password, no two-factor authentication, and no IP filtering.
Once connected, the attacker attempted to modify the sodium hydroxide (NaOH) dosage settings — a base used to balance water pH. The dosage was changed from 100 to 11,100 parts per million, a level potentially toxic to the population if maintained long enough.
Impact
The attack was detected in real time by an on-site operator who observed the mouse moving and settings changing without any local human intervention.
No health consequences were observed:
- The SCADA alarm flagged the threshold breach,
- The treatment process had not yet reached the final injection point,
- And manual correction was immediate.
DATIVE helps you secure your industrial remote access. Request an audit
Remediations
Following the incident, several corrective measures were recommended or implemented:
- Removal of uncontrolled remote access: full audit of remote maintenance tools, deactivation of unnecessary services, IP filtering.
- Deployment of a secure access bastion with logging and strong authentication (MFA) to manage all external access.
- IT/OT network segmentation, with explicit filtering of inter-domain traffic (no direct Internet access to industrial devices).
- Implementation of secure, non-editable thresholds without elevated authorization, configured at the SCADA or PLC level (hard-coded limits).
Lesson learned
The Oldsmar incident is emblematic of a growing concern: critical OT infrastructure exposed to the Internet, insufficiently protected, and often lacking active monitoring.
Two major vulnerabilities clearly emerge:
- Poor remote access management, often implemented without a clear security policy,
- And weak integrity controls on operator actions in outdated or misconfigured SCADA systems.
This case shows that even an unsophisticated attack can pose a major health risk if not detected in time. The operator’s quick response was crucial — but cannot be the only line of defense.
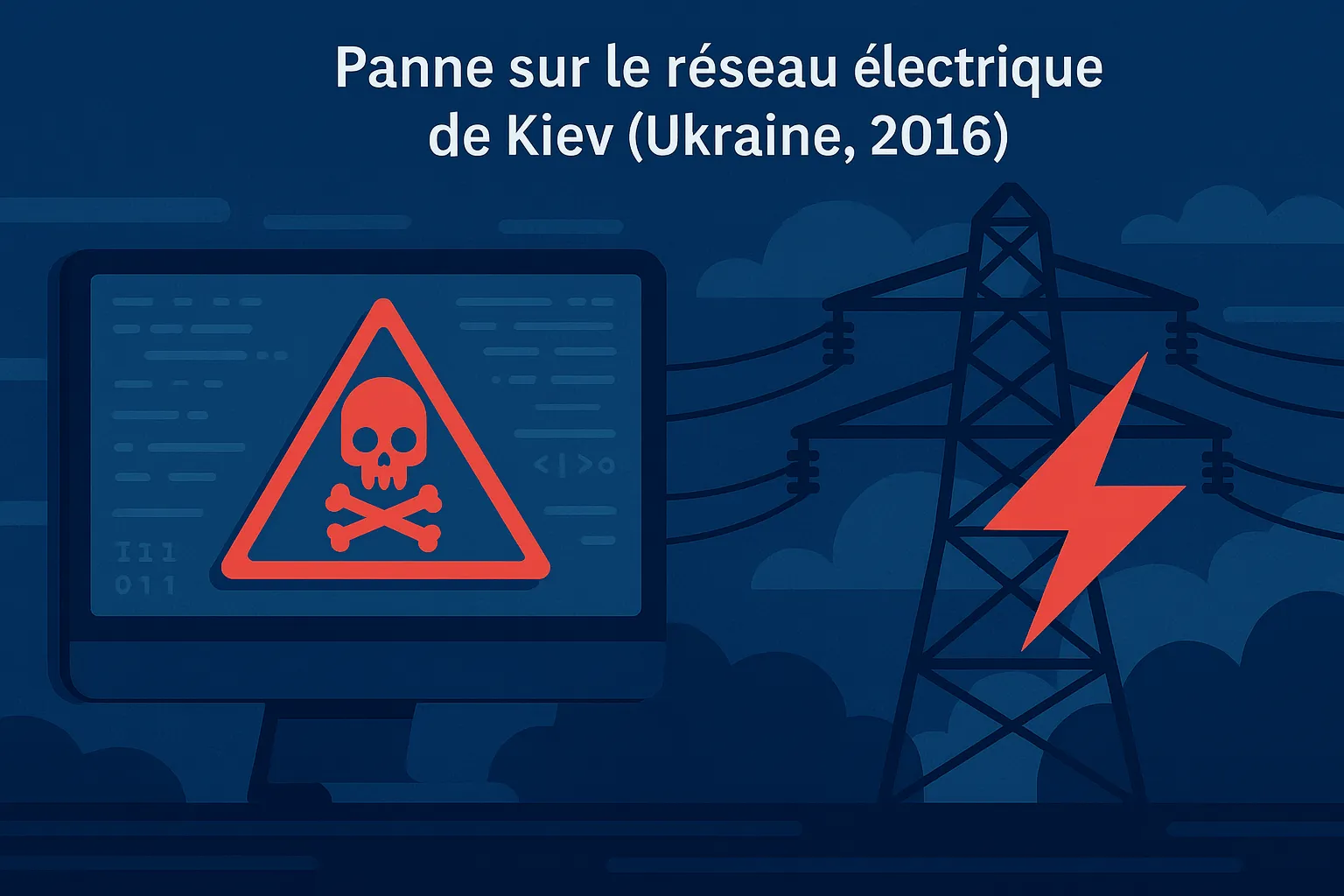
Attack Example #2: Industroyer Cyberattack on Kiev Power Grid (Ukraine, 2016)
Context and vector
On December 17, 2016, several electrical substations in Kiev were paralyzed for about an hour. Analysis by ESET and Dragos revealed the use of a sophisticated malware called Industroyer (also known as CrashOverride).
This malware directly exploited industrial communication standards, including:
- IEC 60870-5-101,
- IEC 60870-5-105
The initial intrusion did not require any 0-day vulnerabilities: the attackers used common penetration techniques (compromised IT workstations, unsegmented access, or poorly secured remote access).
Impact
The attack caused a power outage lasting about an hour, affecting entire districts.
Beyond the immediate interruption, potential consequences included:
- overheating of transformers,
- failure of protection relays,
- instability of the distribution network.
Industroyer aimed not only to cut power, but to conceal its actions in order to disrupt recovery efforts.
Remediations
In response to this type of threat, best practices have coalesced around three main pillars:
- Strict segmentation of SCADA environments to limit lateral movement from IT to OT.
- Monitoring of OT traffic using specialized IDS capable of detecting anomalies in protocols such as IEC 60870-5-104,
- Regular resilience testing through blackout simulations to test team responsiveness and preparedness.
Lesson learned
Industroyer was a milestone in OT malware history:
- It is a framework that directly targets industrial protocols, classified as ICS-targeted malware.
- These malwares don’t need to exploit complex vulnerabilities; they manipulate authorized industrial commands.
- Security therefore relies less on patching, and more on behavioral detection of flows and operational resilience.
Attack Example #3: Triton Attack on a Saudi Refinery (2017)
Context and vector
In 2017, a sophisticated attack targeted a refinery in Saudi Arabia by compromising its Safety Instrumented Systems (SIS).
The malware used, known as Triton, Trisis, or HatMan, specifically targeted Triconex PLCs manufactured by Schneider Electric, used to trigger Emergency Shutdown (ESD) procedures.
The attacker gained access to an engineering workstation connected to the industrial network. From this station, they deployed the Triton malware into the SIS using custom scripts via the TriStation software. The malware could alter embedded safety logic, disabling critical protection functions such as automatic shutdowns in the event of a leak, overpressure, or high temperature.
Impact
Fortunately, the attack did not reach its final objective: a coding error in the malware caused a system crash, leading to an unexpected process shutdown. This incident led the team to uncover the compromise.
The potential consequences were severe:
- Disabling of automatic protection systems,
- Risk of explosion or major industrial accident,
- Catastrophic human, environmental, and economic impacts.
Triton is the first known cyberattack to target not availability, but the safety functions of industrial systems.
Responses and remediations
In response to this kind of threat, both technical and organizational countermeasures were reinforced:
- Comprehensive system audit, including firmware review, embedded logic inspection, and configuration file analysis.
- Systematic software integrity checks to detect unauthorized changes in safety PLCs.
- Enhanced supervision of access to engineering workstations, with logging, MFA, and strict network segmentation.
- Strict separation of office, control (DCS/PLC), and safety (SIS) networks to prevent lateral movement and indirect pivoting.
Recommendations were also issued to limit the use of proprietary protocols, which are often poorly monitored, and to restrict privileges on programming tools such as TriStation.
Lesson learned
Triton represents a paradigm shift in industrial cybersecurity: for the first time, a malicious actor attempted to disable systems designed to protect human lives.
This attack highlights the fact that:
- Engineering workstations are critical targets, often poorly secured.
- Industrial systems are not immune and must be subject to the same monitoring requirements as the rest of the infrastructure.
- Software integrity and physical segmentation remain foundational pillars of OT cybersecurity.
Triton also reveals a growing convergence between OT threats and geopolitical objectives, suggesting a state-sponsored origin (unofficially attributed to a group linked to Russia, according to FireEye).
Attack Example #4: Ransomware attack on the JBS food group (2021)
Context and vector
At the end of May 2021, JBS—the world’s largest meat processing company (beef, pork, poultry)—was hit by a ransomware cyberattack that crippled much of its operations in North America and Australia.
The attack was attributed to the REvil criminal group, known for its targeted campaigns against critical infrastructure.
The initial compromise occurred in the IT environment, escalating into the OT network via poorly segmented interconnections, allowing lateral propagation across domains.
This scenario is typical in companies where industrial systems are connected to business networks for supervision, reporting, or remote maintenance purposes.
Impact
The attack led to:
- Temporary shutdown of dozens of slaughterhouses and processing sites in the U.S., Canada, and Australia,
- Major disruptions to the global agri-food supply chain,
- Closures of several facilities for multiple days,
- And the payment of a $11 million ransom (in Bitcoin), according to JBS statements.
Beyond financial losses, the group’s reputation was damaged, and supply tensions emerged in some markets.
Remediations
JBS implemented several crisis measures in coordination with its cybersecurity teams, external partners, and U.S. authorities:
- Immediate isolation of IT and OT segments, including physical disconnection to stop the spread,
- Reinforced deployment of a SOC with behavioral detection capabilities to detect lateral movement or exfiltration attempts,
- Activation of a global incident response plan across multiple continents, with crisis communication, forensic investigation, and prioritized restoration processes,
- Strengthened offline backups, including immutable copies to prevent encryption of critical data.
Crisis management was rapid but required a site-by-site progressive restart based on the ability to validate system integrity.
Lesson learned
The attack on JBS highlights several key lessons for industrial organizations:
- IT/OT convergence creates cross-domain infection paths if not properly managed,
- An IT-origin attack can directly impact operations, even without malware specifically targeting PLCs,
- Cyber crisis governance must be designed on a global scale, with action plans adapted to multi-site and multi-regulatory contexts.
Lastly, this case reminds us that resilience is not only about technical protections, but also about the ability to detect early, segment effectively, and recover safely.
We design an OT incident response plan tailored to your industrial sites. Contact our experts.
What strategic responses can counter industrial cyberattacks?
OT attacks continue to grow in sophistication. To face them, industrial players must evolve from a classic defensive stance to a proactive, resilient posture adapted to field constraints. This means combining advanced detection technologies, cyber crisis governance, human awareness, and structured compliance.
Early detection to reduce impact: IDS, IPS, and OT SOC
In industrial environments, time works against security. An undetected breach can rapidly escalate into a production incident, or worse, endanger operators.
It is therefore essential to detect weak signals as early as possible. This involves:
- Deploying passive probes (IDS) on OT networks, capable of analyzing industrial protocols (Modbus, S7, IEC 104…),
- Using OT-specific IPS solutions (to be activated with care), in addition to hardened industrial firewalls and switches,
- Centralizing alert correlation through an OT SOC, able to distinguish normal operational behavior from abnormal or suspicious sequences.
Build response plans tailored to industrial realities
Having an incident response plan is essential. But in OT, it cannot simply replicate IT standards. An effective response must involve:
- Realistic crisis scenarios aligned with incident types specific to the industrial environment,
- Regular testing (e.g., table-top exercises, red teaming, blackout simulations),
- Operational fallback procedures accounting for machine dependencies, cycle times, and process safety constraints.
In OT, a good response plan is above all one that teams can execute in degraded conditions without endangering production or personnel.

Strengthening the human factor: the first firewall is your team
An attack doesn’t always require a technical exploit. An unlocked engineering workstation, a shared password, or an untrained contractor may be enough.
Investing in operator awareness, ongoing training for automation engineers, and control over third-party access is often underestimated, yet remarkably effective.
The OT security culture must reach the shop floor—into workshops, production lines, and maintenance teams. Not just the CISO’s office.
Need help improving your resilience against OT attacks? Contact us
Integrating compliance into your industrial cybersecurity strategy
Regulatory obligations are no longer optional. With the growing influence of NIS2, the Military Programming Law (LPM), and standards such as ISO/IEC 27001 and IEC 62443, industrial players must demonstrate their ability to:
- Detect incidents,
- Respond effectively,
- Recover quickly,
- And learn from the event.
Compliance is becoming a governance issue: it shapes investments, priorities, and relationships with authorities and strategic clients.
FAQ
Question 1: Why document an OT incident if no direct impact was observed?
Even without visible impact, an incident reveals technical, human, or organizational weaknesses. Documenting these weak signals helps strengthen resilience, feed risk analysis, and prevent more serious scenarios.
Question 2: What is the difference between an IT and an OT incident response plan?
An OT plan accounts for process safety constraints, real-time logic, machine dependencies, and HSE requirements. It must function offline and be executable by field teams without cybersecurity expertise.
Question 3: What types of OT probes can be deployed without impacting production?
Passive probes (industrial IDS) can be installed on SPAN or TAP ports. They analyze network traffic without interfering with it. They detect anomalies in industrial protocols (Modbus, S7, IEC 104…) without slowing down PLCs.
Question 4: Does NIS2 apply to all industrial sites?
No. It primarily concerns Operators of Essential Services (OES) and critical entities. However, many industrial companies—even mid-sized ones—are now included. A compliance audit helps clarify the obligations.
Question 5: How can DATIVE strengthen the cybersecurity of my industrial site before an attack occurs?
DATIVE offers a proactive, context-driven approach:
- Complete mapping of your OT environments and industrial flows.
- Cyber maturity and risk assessment (ISO 27005, EBIOS, IEC 62443).
- Deployment of tailored measures: segmentation, hardening, passive monitoring, access control.
- Team training and development of realistic, tested OT response plans. Our goal: to make your site resilient, compliant, and fully operational.
Contact DATIVE today to strengthen the resilience of your industrial sites





