
Vulnerability Management in Industrial Systems (OT): From Theory to Real-World Practice
Managing security vulnerabilities in industrial systems has become a key challenge — but one that’s rarely straightforward. With legacy equipment, unpatchable systems, and often incomplete inventories, field teams must navigate significant technical and operational constraints. While standards and frameworks provide valuable guidance, applying them in real industrial environments remains complex. This article explores the real-world obstacles and presents a pragmatic approach to effectively securing existing systems without disrupting operations.
Why is OT vulnerability management so complex?
Vulnerability management in industrial systems (OT) differs significantly from classical IT approaches.
A challenging operational reality
On the ground, industrial teams face recurring challenges:
- Obsolete equipment no longer supported by vendors (e.g., Windows XP or 7 systems, legacy Siemens and Schneider PLCs).
- Unavailable or hardly applicable patches, often bundled with functional updates that risk causing regressions in production processes.
- Frequent lack of visibility over actual network assets. Many industrial clients have a partial or complete loss of control over their OT inventory.
These operational constraints significantly limit the ability to fully implement cybersecurity best practices. In OT security, you simply cannot protect what you don’t accurately know.
Practical barriers observed during OT audits
During our audits at DATIVE, we consistently identify critical vulnerabilities—well-known but often ignored or unpatched in real environments:
- Very old industrial PLCs, in use for 10 to 15 years, without any updates for several years.
- Supervisory stations running Windows 7, with full admin rights, no antivirus, and no security patches.
- Networks using public IPv4 ranges, exposing industrial equipment directly to the Internet, and frequently misconfigured or unmonitored IPv6 connectivity, which can also be exploited.
These recurring vulnerabilities directly expose companies to production shutdowns or major compromises of their OT systems.
Have your OT infrastructure audited by DATIVE today
The illusion of a complete inventory in industrial environments
Why traditional inventory falls short
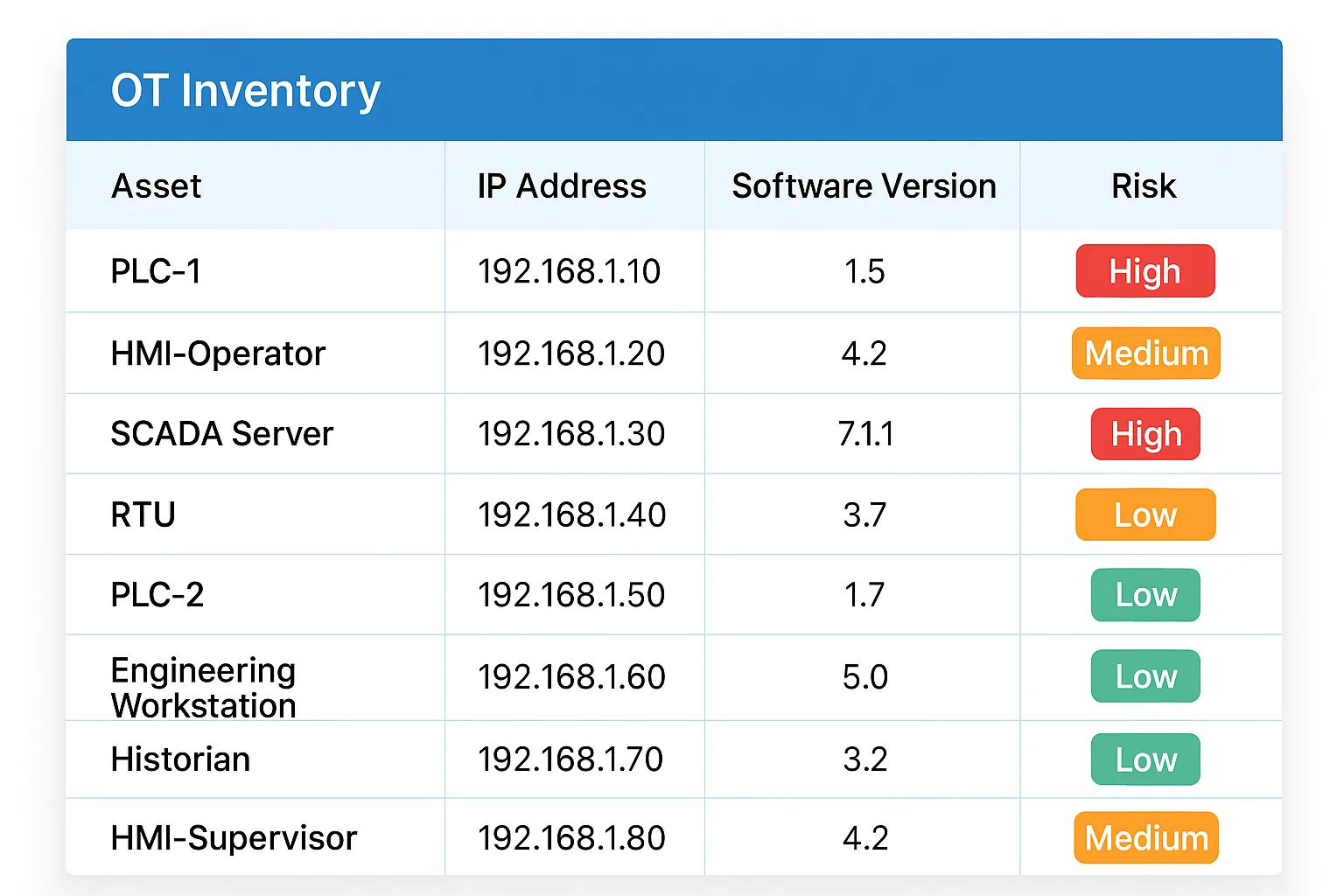
An effective OT inventory goes far beyond a basic list of IP addresses or devices. Yet in practice, this is still the norm on the field.
A true OT inventory that aligns with best practices must support proactive vulnerability management and include the following data:
- Manufacturer, model, and exact reference of each device.
- Accurate versions of OS, firmware, and installed software.
- Functional role and business criticality level within the production chain.
- Real network exposure (inbound/outbound flows, active protocols, open ports).
- Interdependencies and links with other industrial assets.
- All related network information: subnets, VLANs, MAC addresses, etc.
- Physical connections (ports in use, physical location, cabinet IDs, actual cabling).
Without this level of detail, it is impossible to properly prioritize risks or automate vulnerability tracking. An incomplete inventory creates critical blind spots for cybersecurity.
Get a precise OT inventory with DATIVE
Operational risks of an incomplete inventory
An incomplete inventory is more than an administrative flaw—it’s a true operational threat. It leads to unawareness of existing vulnerabilities, making it impossible to anticipate real threats.
In the field, we frequently observe high-risk scenarios due to incomplete inventories, such as:
- An obsolete, undocumented industrial network device exposed to the Internet via a public IPv4 address, with known vulnerabilities for years.
- A Siemens or Schneider PLC with firmware over 10 years old, active on the network but missing from the inventory—ideal for targeted cyberattacks.
- An abandoned supervisory workstation running Windows XP or 7, with admin rights and unsecured remote access (TeamViewer, VNC, etc.), forming a direct entry point to the OT network.
These are not theoretical risks—they happen regularly and are exploited during real-world attack campaigns. Without a full inventory, these flaws remain invisible until they’re successfully exploited—often too late and at great cost. New directives like NIS2 now require you to maintain detailed inventories and maps of your OT systems.
A complete inventory is not just best practice—it’s an operational necessity for industrial continuity and cybersecurity.
The DATIVE pragmatic method for OT vulnerability management
To address these challenges, DATIVE applies a structured four-step methodology.
Step 1 – Mapping and exhaustive inventory of OT equipment
We perform comprehensive field mapping using:
- On-site presence to identify equipment.
- Passive and semi-active audit without disrupting production.
- Detection of exact OS and firmware versions.
- Precise identification of network flows and business dependencies.
Step 2 – Automated correlation with public CVE databases
Collected data is correlated with:
This correlation enables immediate identification of critical vulnerabilities applicable to actually deployed equipment.
Step 3 – In-depth analysis of real-world exploitability
Not all vulnerabilities are immediately exploitable. We assess:
- Effective network exposure of vulnerable devices.
- Presence or absence of compensating controls (network segmentation, OT firewalls, IDS).
- Realistic attack paths within the actual industrial environment.
Step 4 – Business-based prioritization and pragmatic recommendations
We build a prioritization matrix based on:
- Intrinsic technical severity of each CVE.
- Actual exploitability in the field.
- Concrete business impact in case of compromise.
This approach helps industrial teams focus their efforts on the truly critical vulnerabilities.

OT vulnerability management cannot remain a theoretical exercise. It must be concrete, pragmatic, and fully embedded in operational processes.
At DATIVE, we help clients overcome field constraints with targeted, realistic, and effective actions.
Contact our experts today





