
These workstations will never be patched… but they can become unalterable
This article presents a comprehensive hardening strategy for obsolete workstations to strengthen your industrial cybersecurity. In industrial environments, we regularly encounter outdated systems (Windows 2000 SP4, XP, 7 or old Windows 10). These systems, although critical in industry, can no longer receive patches: license issues, PLC incompatibilities, or risk of production shutdown.
If your production line is affected by obsolete workstations (and it most likely is), this article details how we deploy a hardening strategy to transform these systems into secure bastions—without compromising industrial continuity. You will discover:
- Why these obsolete workstations are still in production.
- What risks they pose to your industrial cybersecurity, particularly through vectors such as uncontrolled secure USB.
- How to implement a hardening method with whitelisting, system lockdown, monitoring, and auditing.
Why hardening is often the only realistic lever in OT
In the world of IT cybersecurity, responses are often binary: migrate, virtualize, or completely isolate.
But in OT, room for maneuver is much narrower. Field constraints, availability requirements, and interdependencies with automation make any invasive operation complex—or even impossible.
Here’s why hardening is often the only short-term realistic option:
- Migration is rarely possible without recoding processes: Many legacy industrial applications are frozen, without updates or support. They rely on a specific version of Windows. This dependency is often technical: hardware driver, PCI card, PLC, or integrated SCADA. Migrating would require full functional revalidation—a long, costly, and risky process.
- Virtualization often requires a reboot: In industry, it’s not uncommon for a system to have been running non-stop for years. A reboot alone can crash the environment, reset a license, or corrupt a critical configuration file.
- IT security doesn’t apply directly: EDR, SIEM, NAC, or centralized patching are ineffective (or incompatible) with these older OS versions. IT teams are often powerless when no agent can be deployed on these systems.
- The human factor is key: Operators use these systems daily. Modifying interfaces, restricting use without support, or even changing a shortcut can cause rejection. Non-intrusive hardening, when well executed, does not alter ergonomics or habits. It is an invisible but effective barrier.

Why obsolete workstations persist in industry
Technical and economic constraints
Critical industrial systems often depend on an outdated operating system. This can be due to non-transferable licenses or unmanageable industrial drivers. Replacing these workstations sometimes means risking prolonged downtime. As a result, many Windows XP or Windows 7 machines remain in service. Faced with these constraints, hardening obsolete workstations becomes a concrete alternative to impossible migration.
Operational risk of updates
Updating a critical workstation may break communication with a PLC. It may also cause API errors or crash the process. Paradoxically, avoiding migration becomes the safest option to maintain production.
Need an audit of your obsolete systems? Contact our DATIVE experts today.
Associated industrial cybersecurity risks
Unpatched vulnerabilities
These obsolete systems no longer receive official patches. Known vulnerabilities (SMB v1, EternalBlue, etc.) remain exploitable. They are not compatible with modern EDR, leaving your OT infrastructure exposed to persistent threats.
Easy intrusion vectors
Without hardening, the cyber threats we regularly encounter come from:
- Uncontrolled USB drives,
- Injected scripts or unauthorized DLLs,
- Local privilege escalation.
These methods offer easy access to attackers seeking to target your industrial chain.
Obsolete ≠ lost: a digital containment strategy
This is where hardening obsolete systems becomes meaningful.
Objective of hardening: an unalterable workstation
The goal is not patching, but locking down the system:
- Strict whitelist of executables, DLLs, scripts,
- Blocking any non-referenced file, including locally,
- Granular USB control (read-only, audit, block),
- System lockdown according to business use,
- Continuous monitoring and alerts on abnormal behavior.
Practical hardening deployment on process workstations
At DATIVE, on a Windows XP supervision workstation, we deploy:
- Active application control with dynamic whitelisting,
- Secure USB module in read-only or total block mode,
- Restrictive network filtering (authorized IPs, business ports only),
- Centralized logging for audit and traceability.
This turns your critical workstation into a stable, compliant, and secure system—even without migration.
Virtualization or hardening? Two approaches, two constraints
When addressing OT obsolescence, two technical responses are often considered: virtualizing the existing OS, or hardening in place. These options do not serve the same purposes and are not interchangeable.
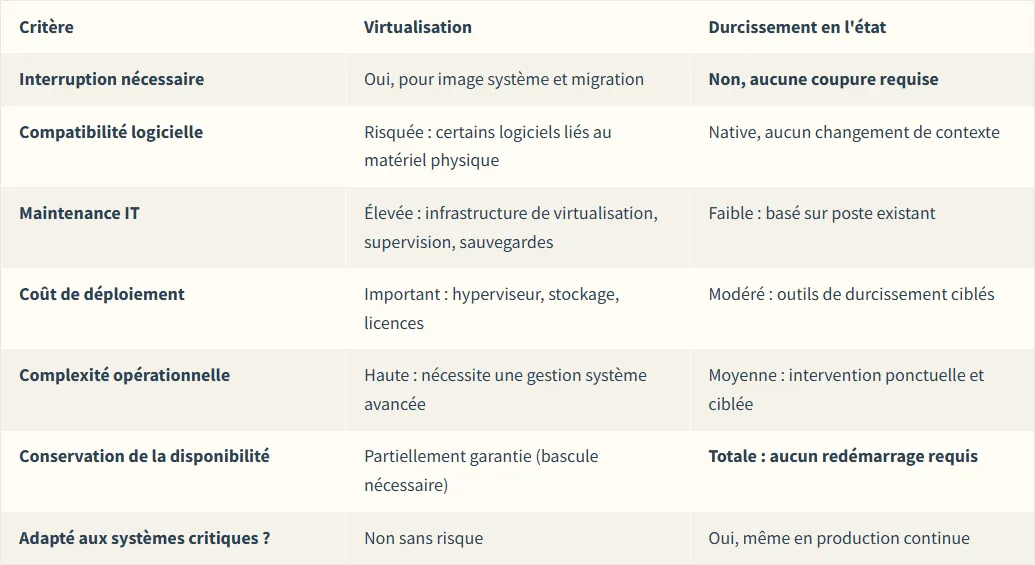
Virtualization can be relevant for non-critical or lightly used systems. But for a critical, continuously running workstation that cannot be stopped or reconfigured, hardening is the only method that preserves availability while significantly increasing security.
Hesitating between virtualization and hardening? Request a feasibility study from our DATIVE experts through this contact form.
Integrating hardening into 360° OT governance
When to apply hardening
- When migration is impossible or planned beyond 12 months,
- If the critical workstation depends on a legacy application or PLC,
- When exposure is high (network connectivity, frequent USB use).
Governance model
- Clear roles (MOA, MOE, CISO),
- Logging of actions and modifications,
- Secure maintenance procedures (temporary disabling of the hardening cage).
Thus, targeted hardening becomes an active measure, not a compromise.
Positioning on OT technical debt
An obsolete workstation is only dangerous if it is exposed or uncontrolled. On the contrary, a hardened legacy workstation can run for years without increased risk.
This ties into best practices covered in our articles:
- The Trends and tools in industrial cybersecurity – 2025, on workstation lockdown and real-time network monitoring.
- The 5 best practices to improve your industrial cybersecurity, including IDS/IPS probes and network segmentation.
- The NIS2 Directive and industrial cybersecurity stakes, reinforcing the need to secure legacy systems.
Conclusion
Obsolete workstations are inevitable in OT environments. But they are not unsalvageable. Thanks to hardening, it is possible to protect them effectively without immediate migration.
At DATIVE, we help you to:
- Diagnose your legacy systems,
- Implement hardening policies including whitelisting, monitoring, secure USB, and granular lockdown,
- Integrate this strategy into your industrial cybersecurity governance.
Facing a similar challenge? Contact our experts for a free assessment, audit, or operational support.
Hardening obsolete systems allows you to combine operational continuity with pragmatic security.
Hesitating to harden a Windows XP or 7 fleet? DATIVE supports you in risk assessment, hardening policy definition, and on-site or remote implementation.
FAQ – Obsolete workstations and industrial cybersecurity
Question 1: Can a Windows XP or Windows 7 workstation still be used in production in 2025?
Yes, provided it is strictly isolated, hardened, and integrated into a coherent industrial cybersecurity policy. Whitelisting, USB control, and activity monitoring allow these systems to remain within a secure framework.
Question 2: What’s the difference between hardening and patching?
Patching fixes a vulnerability at the source by modifying the OS. Hardening locks down the workstation’s behavior to reduce attack surfaces without modifying the system. This method is ideal when patches are no longer available (as with obsolete systems).
Question 3: What can be done if an obsolete workstation is connected to a supervision network?
It is crucial to control network flows upstream: local firewalls or industrial VLANs, limitation of ports, IPs, and protocols used. DATIVE also recommends systematic logging and network segmentation, as covered in this article.
Question 4: Is USB port blocking systematic?
No. It is possible to implement secure USB control: some ports can be read-only, others completely disabled, with temporary authorization during maintenance through controlled procedures. This flexibility balances security with industrial operations.
Question 5: What is the typical cost of a hardening project for obsolete workstations?
The cost depends on the number of systems, their role in the OT architecture, and the required level of security.





